#atlantis (2021-04)

| Discuss the Atlantis (<http://runatlantis.io | runatlantis.io>) |
**Archive: ** https://archive.sweetops.com/atlantis/
2021-04-01
Thanks for contributing Pre Workflow Hooks!
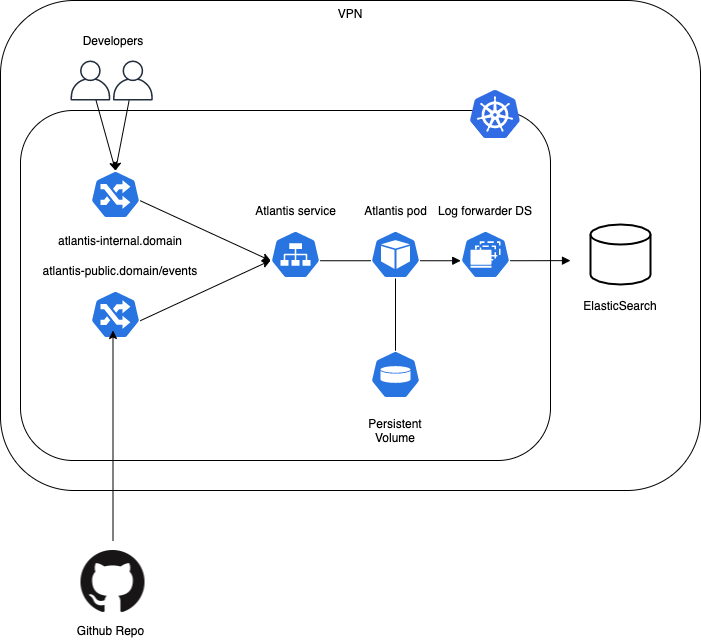
Structured logging sounds great too.
2021-04-02
2021-04-08
if a module A changes, how can i tell atlantis to do a plan in modules B, C, and D which consume the changed module A ?
That’s not possible in vanilla Atlantis
It is supported by spacelift
ahhhh very cool
If you use terragrunt and atlantis this is the default behavior if you use https://github.com/transcend-io/terragrunt-atlantis-config (disclosure: I maintain that repo)
Generate Atlantis config for Terragrunt projects. Contribute to transcend-io/terragrunt-atlantis-config development by creating an account on GitHub.
I’ll check it out. Thanks David
2021-04-15
has anyone setup infracost with atlantis using the upstream terraform module?
infracost have integration with atlantis
check the docs
it was released no long ago
yeh i am trying to get it to execute but can’t seem to get it working
workflows = {
default = {
plan = {
steps = [
"init",
"plan",
{ run = "/home/atlantis/infracost_atlantis_diff.sh" }
]
}
apply = {
steps = [
"apply",
{ run = join(" && ", local.update_deploy_tag) },
]
}
}
}
is the scrip chmod +x?t
its inside their upstream container
ahhhh ok
i am basing it off https://github.com/infracost/infracost-atlantis/
i think i may have seen it
2021/04/15 21:31:05+0000 [DBUG] run_step_runner.go:71 XXXX/tf-env-k8s#81: Error: exit status 1: running "/home/atlantis/infracost_atlantis_diff.sh" in "/home/atlantis/.atlantis/repos/XXXX/tf-env-k8s/81/default/eu-west-1-data-engineering-prd":
do: bash -x /home/atlantis/infracost_atlantis_diff.sh
Is there an estimate on a stable 0.17 release? We are particularly waiting for the https://github.com/runatlantis/atlantis/pull/1418 fix to be released
Allows you to actually do dynamic configuration generation since unlock command can be run at anytime which would then nuke the working directory and the PR would need to be opened again from scratch.
guess what it is going to happen today…..
Allows you to actually do dynamic configuration generation since unlock command can be run at anytime which would then nuke the working directory and the PR would need to be opened again from scratch.
Yay
I think this release will take a bit longer since that feature is fairly big so it needs more testing
Just curious, what testing is going on? I haven’t seen many issues created related to the beta and its been well over a month since its release
2021-04-19
is anyone using https://github.com/terraform-aws-modules/terraform-aws-atlantis with azure AD for OIDC?
Add support for parallel plans and applies (#926 by @Fauzyy)
Running in parallel is only supported if you’re using workspaces to separate your projects.
Projects in separate directories can not be run in parallel currently.
To use, set
parallel_plan: true
parallel_apply: true
In your repo-level atlantis.yaml file.
does anyone know if this is/will be supported when using seperate directories?
Nope, #260 is still open https://github.com/runatlantis/atlantis/issues/260
It works so long s you use different workspaces per directory, right? We have dozens of plans run in parallel from different directories
2021-04-20
@David how’d you mean?
2021-04-21
using https://github.com/terraform-aws-modules/terraform-aws-atlantis can someone explain to me how I can update atlantis-ecs_task_execution so it has privileges to assume roles in other accounts? something like https://github.com/terraform-aws-modules/terraform-aws-atlantis/issues/145 ? struggling with this at the moment
@Steve Wade (swade1987) can you help here?
@Piotr Hryszko sure let me create a gist once i am off this call
can you gimme 20 mins?
thanks! let me try this out!
worked perfectly, thanks!
2021-04-22
does anyone know with the latest https://github.com/terraform-aws-modules/terraform-aws-atlantis how to use authentication to work with gitlab ?
Terraform configurations for running Atlantis on AWS Fargate. Github, Gitlab and BitBucket are supported - terraform-aws-modules/terraform-aws-atlantis
are the docs in https://github.com/terraform-aws-modules/terraform-aws-atlantis/tree/master/examples/gitlab-repository-webhook helpful ?
Terraform configurations for running Atlantis on AWS Fargate. Github, Gitlab and BitBucket are supported - terraform-aws-modules/terraform-aws-atlantis
ive used that module to configure it with github as an atlantis bot but never with gitlab
Got it working had to add the gitlab cidr blocks to the unauth endpoints on the ALb