#aws (2023-08)
 Discussion related to Amazon Web Services (AWS)
Discussion related to Amazon Web Services (AWS)
 Discussion related to Amazon Web Services (AWS)
Discussion related to Amazon Web Services (AWS)
Archive: https://archive.sweetops.com/aws/
2023-08-01
Dear colleagues, what’s the correct way to create a ROLE that would enable LAMBDA hosted in eu-central-1 to USE ECR IMAGE hosted in eu-central-2 ? Thanks a lot
You need cross account roles. A resource role on the ECR repository and a role for lambda giving it ECR permissions. More details at https://aws.amazon.com/blogs/compute/introducing-cross-account-amazon-ecr-access-for-aws-lambda/

This post is written by Brian Zambrano, Enterprise Solutions Architect and Indranil Banerjee, Senior Solution Architect. In December 2020, AWS announced support for packaging AWS Lambda functions using container images. Customers use the container image packaging format for workloads like machine learning inference made possible by the 10 GB container size increase and familiar container […]
Dont need a cross account role if its in the same account. Roles are global and not regional too.
2023-08-02
2023-08-03
View the overall status and health of AWS services using the AWS Health Dashboard.
Some are reporting issues affecting autoscaling
View the overall status and health of AWS services using the AWS Health Dashboard.
2023-08-10
Hi, when I try to invoke one apigateway in another apigateway through http proxy of two different aws accounts, I am getting not authorized errors since my resource policy is restricted to only our network and client network, but request ip is getting from AWS public range( since apigateway is public), is there a way to solve this. Thanks
Provides an overview of API Gateway private APIs.
Hi all! I’m trying to have a central API Gateway in an Infrastructure AWS account, where different base paths from the API can be redirected to the respective apps, deployed in separate AWS accounts, but to the same VPC (shared between accounts). Currently, I have no way for the ECS in the AWS accounts to have permission to register in the target group created in the Infrastructure account (with error: Unable to assume role and validate the specified targetGroupArn).
As Target groups do not support resource policies, I don’t think it’s possible to achieve something like this? I wanted to avoid: 1) having multiple separate API Gateways, to centralize its configuration and certificate management in the Infra account, and 2) having duplicated costs because of each app having their own NLB
you need to use a diff TF aws provider and use it to provision the TargetGroup attachments. The provider should assume a role from the other account
similar to:
resource "aws_lb_target_group_attachment" "nlb" {
count = length(local.nlb_network_interface_private_ips)
target_group_arn = local.alb_target_group_arn
target_id = local.nlb_network_interface_private_ips[count.index]
availability_zone = "all"
port = var.port
# The attachment of the NLB private IPs to the ALB Target Group is provisioned in the ALB account
provider = aws.alb
}
provider "aws" {
alias = "alb"
region = var.region
assume_role {
role_arn = <role from the Infrastructure account>
}
}
Thank you, Andriy!
So, if I understand correctly, this would mean going API Gateway -> NLB -> ALB for ECS service. The NLB target group would be of type alb (type ip would be a hassle to maintain, and ecs_load_balancers variable from here can’t be used because of needing a different provider)
dynamic "load_balancer" {
for_each = var.ecs_load_balancers
content {
container_name = load_balancer.value.container_name
container_port = load_balancer.value.container_port
elb_name = lookup(load_balancer.value, "elb_name", null)
target_group_arn = lookup(load_balancer.value, "target_group_arn", null)
}
}
the above was just an example on how to use a diff provider to assume a role into the other account to provision the TargetGroup attachments in it. The example does not mean you have to use NLB and ALB , use whatever resources you need
Trying to go with an alb Target Group doesn’t work, because:
• When trying to create the aws_lb_target_group_attachment resource, by assuming the role for the Infra account (who owns the Target Group), fails because it doesn’t know about the load balancer set as the target_id. Error: registering targets with target group: ValidationError: ‘arn:…’ is not a valid load balancer ARN
• When trying to create the aws_lb_target_group_attachment resource, by assuming the role for the App account (who owns the ALB), fails because it doesn’t know about the target group set as the target_group_arn. Error: registering targets with target group: ValidationError: ‘arn:…’ is not a valid target group ARN
How willing are you to trying new/unproven tech? Your use case sounds like lattice: https://aws.amazon.com/blogs/networking-and-content-delivery/build-secure-multi-acco[…]c-connectivity-for-your-applications-with-amazon-vpc-lattice/

Introduction In this blog post, we will discuss how you can use Amazon VPC Lattice to connect your services securely, and monitor communication flows, in a simple and consistent way across instances, containers, and serverless, in a multi-account and multi-Virtual Private Cloud (VPC) environment. We’ll define the new constructs VPC Lattice leverages to enable application […]
Hi @Michael Manganiello Was the use case above enough to make it work?
2023-08-11
https://aws.amazon.com/about-aws/whats-new/2023/08/amazon-ec2-m7i-flex-m7i-instances/ did anyone test new -flex instances? how do they compare to burstable (t3) instances?
2023-08-12
AWS now supports Security groups on network load balancers.
https://aws.amazon.com/about-aws/whats-new/2023/08/network-load-balancer-supports-security-groups/
I love this feature. But does cloudformation support it yet?
Very good question. I suspect terraform will be a little behind on this.
Terraform is usually pretty on the ball with minor enhancements like this. Maybe two weeks? I’d be surprised if it takes longer… https://github.com/hashicorp/terraform-provider-aws/issues/32982
Description
aws just announced that it support security group in network load balancer, hence aws_lb resource may need enhance to support this feature, tested from aws console can config it now
https://aws.amazon.com/about-aws/whats-new/2023/08/network-load-balancer-supports-security-groups/
Affected Resource(s) and/or Data Source(s)
aws_lb
Potential Terraform Configuration
No response
References
https://aws.amazon.com/about-aws/whats-new/2023/08/network-load-balancer-supports-security-groups/
Would you like to implement a fix?
None
2023-08-14
Hi all, I am trying to review how we grant access to user on our AWS environment, there has been cases where users spin up services and forget to turn them off. We have implemented a cron job to delete services left running with a nuke tool, however, I am wondering if there is a fine grain approach to managing the access or if anyone can share some experience, that will be helpful.
I’ve heard good feedback about https://opal.dev/ but we are not using it so cannot share personal experience
.png)
Opal is the identity security platform for modern enterprises. With Opal, companies can implement least privilege, automate access reviews, and accelerate access requests.
Has anyone successfully rolled their own Just In Time access for elevated permission through AWS Identity Center? I’ve seen this post on the AWS blog, but it seems like… I dunno? a lot? lol

September 9, 2022: This blog post has been updated to reflect the new name of AWS Single Sign-On (SSO) – AWS IAM Identity Center. Read more about the name change here. March 23, 2022: In the section “Logging session activity,” we fixed an error in the CloudTrail example and added a note of explanation. In […]
IMO this is definitely something you pay a SaaS for https://www.commonfate.io/
We don’t use the above but I trialled it extensively and liked it.

Automate and secure permissions to your infrastructure and internal applications. Enable fast workflows for access when it’s needed.
yes, there are vendor integrations available now too. For example for Okta and few more
if you want more options we build this open source terraform module to manage JIT access via Slack https://github.com/fivexl/terraform-aws-sso-elevator
Slack bot to temporary assign AWS SSO Permission set to a user
yeah, I’m definitely looking for an open source implementation. Wish I could just buy something lol
@andrey.a.devyatkin thank you for the solution. After spending a bit of time digging into sso-elevator, y’all put a lot of work into this and it’s very nice
at the moment, I think we’re wanting have the authorization path outside of slack
I was also thinking about leveraging an eventbridge scheduler to remove users after a set amount of time
This is not an area I have first hand experience in but it’s something I’ve been interested to learn more about
But I would stay hard away from anything involving rolling your own aws serverless infrastructure.
- If you mess it up you can have big problems
- Even if you don’t mess it up, how many engineers will there be in 2,5,10 years who will want to and be able to not mess it up
- It’s not an aws specific problem. I doubt aws is the only accounts you have.
- Bootstrap problems. You’ll need elevated JIT access to restart your elevated JIT machine
@kallan.gerard definitely valid concerns, people can introduce security problems at any level of the infrastructure that they have the ability to change. I think it comes down to training, tradeoffs and intentions for move things forward
I’m currently in the research phase for this project and I think it will come down to effort vs impact on whether we’ll plan to move forward with it
If it helps give any context I know of atleast one 9 figure tech company that uses SlackOps for aws JIT
We use AzureAD as an identity federation source and for JIT access we use AzureAD Identity Governance which already has all the approval workflows built in. Because all our IAM permisions are using AAD group memberships via Permission Sets, users can request temporary membership in AD groups in Identity Governance portal.
kinda crazy that Azure has this before AWS, good work Microsoft
@Joe Perez tbh it makes perfect sense to me.
Remember we’re talking about separate things.
Microsoft Azure AD is an Identity and Access Management product, grown from the decades old on-premise Active Directory solutions.
Microsoft Azure is akin to Amazon Web Services and Google Cloud Platform. Azure AD technically is a product under the umbrella of Azure, but it’s really a seperate top level product. It would be less confusing if they just called it Microsoft AD as it’s really what it is. Azure AD is akin to Google Groups.
Amazon doesn’t really have a real candidate in this race. Their cloud IaaS platform is obviously aws, not the corporate everything solution that Microsoft (AD, Office 365 etc) and Google (Gmail, Meet, Docs etc) operate at.
It’s very common and sensible for people to use Azure AD as their Identity provider source for aws, which handles human and machine access.
Hence why I recommended avoiding anything at the aws solution as it’s not an aws problem.
The source of your corporate identities is the driving factor.
There’s also https://aws-samples.github.io/iam-identity-center-team/ which I think is the follow-up implementation of the blog from AWS you linked.
Documentation for AWS Temporary Elevated Access Management (TEAM)
2023-08-15
*For members who speak/understand Spanish:* We would like to extend an invitation to you for this virtual session that covers the “AWS Cloud Experience” event in Bogota.
Discover all the in-depth information about the event, including discussions with Cuemby’s CRO, José Rodríguez, and Cast AI’s Latin America Business Leader, José Peña!
This session will provide valuable insights into the key conversations and developments that have emerged, and how they impact the current technology and business landscape in the region.
To stay informed, please click on this link.
How do you usually authenticate to AWS?
i would split those questions in to two parts. First being - what type of AWS creds do you use with answers going like this - static iam, root (surprisingly a lot people still do that), aws sso, static iam + role chaining, etc; and the second part of the poll being - how do you manage/obtain your aws credentions with anwers like aws cli sso, .aws/config, aws-vault, etc; otherwise you are mixing apples and potatoes
great feedback @andrey.a.devyatkin I’ll do that
Followup: is there any limitation currently with your workflow that you would like to see improved? I’m trying to think of ways to improve how we use the AWS authentication daily
@diogof Do you want feedback from @andrey.a.devyatkin ?
yes sure @Gabriela Campana (Cloud Posse)
@andrey.a.devyatkin can you please provide feedback?
feedback for what?
Followup: is there any limitation currently with your workflow that you would like to see improved? I’m trying to think of ways to improve how we use the AWS authentication daily
2023-08-16
2023-08-17
2023-08-18
2023-08-19
2023-08-20
2023-08-22
for aurora serverless v2. when I would like to use TLS connection from client… do I need to get the CA cert locally?
I am believe the TLS certificates are the same for RDS clusters for all accounts. They are scope to a region. You can download the certificates using the links in the documentation.
https://docs.aws.amazon.com/AmazonRDS/latest/AuroraUserGuide/UsingWithRDS.SSL.html
Create encrypted connections to your Amazon Aurora DB cluster using SSL/TLS.
Hi everyone.
is there a Cloudwatch metric to obtain the size of the AWS Opensearch indexes ? I have been looking at the documentation but I can’t find anything related to it.
if it does not exist, do you know of a workaround to implement this? since I really need to alert in Grafana when the indexes exceed a certain size.
Currently the datasource is Aws Cloudwatch
You might need to write your own lambda that uses the _cat/indices API and send it formatted to cloudwatch. Make sure to limit your permissions to only the API that you intend to use. see: https://www.elastic.co/guide/en/elasticsearch/reference/current/cat-indices.html
Thanks @elvis lim!
2023-08-24
2023-08-28
hello all, with basic support how could I ask aws to delete a stuck rds instance? I am testing the global database and when I created the secondary, it stuck in creating. I cannot remove from global database and cannot delete. Any idea?
If you are using global database. . Pay for support
so using global database in prod is not good idea w/o support ? or why do you recommend to pay for support ?
I would always recommend paying for support. And especially if you use the extremely proprietary components of AWS. Global database is one of those things
Hey team! Do you have a good example of a CloudFormation template that creates an EC2 instance with SSM connect configured? Specifically, it should include an IAM role/profile that allows a connection to the instance using SSM from the AWS web console. Any Linux OS works (AMZ Linux 2 or 2023; Ubuntu). I just need to share a template to someone so they can connect to an instance without creating an SSH key.
This article was helpful in getting me to where I needed to be….
https://www.radishlogic.com/aws/cloudformation/cloudformation-ec2-with-iam-role-template/
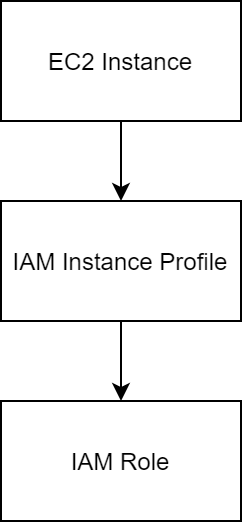
Creating an EC2 Instance with an IAM Role is easy when you do it via the AWS Console but doing this with CloudFormation is not as direct. You will need an Instance Profile to connect an EC2 with an IAM Role. TL;DR: See the CloudFormation Template below. CloudFormation Template What is an Instance Profile? Testing … Continue reading EC2 with IAM Role: CloudFormation Sample Template
2023-08-29
Hello #aws team,
I have bamboo application hosted in ec2, i want to give access to the dev team who are working from home, But i dont want to neither whitelist their individual ip nor to go with VPN configuration aswell. Is there any other approach to achieve this access?? As of now i had given access through workspace, the user will login and access. I am thinking its a complex approach, so looking for some easiest way…
just to note, we aren’t an AWS team. We’re AWS customers who help each other out.
There are a number of solutions here. In general though, they will be classed as “VPN” solutions. If you are worried about the pain and complexity of managing OpenVPN I hear you, and I suggest you look at more modern tools like Teleport or Wireguard
Aws verified access
tailscale is great, or cloudflare access + tunnel if you have cloudflare or want to signup for that
I’ve recently been playing with OpenZiti - it’s an open source, zero-trust access solution. It’s fairly new, so it’s a bit rough around the edges, but it’s working really well for me in a similar use case.
Thanks all for the support, let me check all the possibilities and update which is more feasible for the usecase….
