#general (2021-01)
General conversations related to DevOps/Automation
General Discussions
2021-01-01
Hey everyone, give a warm welcome to our newest members!
- @Jeff Everett
Good to have you here =)
2021-01-02
Hey everyone, give a warm welcome to our newest members!
- @Yashodhan Ghadge
- @Gene Fontanilla
Good to have you here =)
2021-01-04
Hey everyone, give a warm welcome to our newest members!
- @Chris F
- @Adam
- @Nenad Strainovic
- @Pat M
Good to have you here =)
 4
42021-01-05
Hello All! Julian here, trying to learn the latest and greatest of DevOps practices and incorporate them into my architecture for the ultimate in AWS Wizardry. 
Hey everyone, give a warm welcome to our newest members!
- @Robinlemonz
- @winslow cuthbert
- @Uri Unger
- @Julian
- @Prashanth Dudipala
- @vtnvarma
- @khabbabs
- @marttila.riku
Good to have you here =)
 4
42021-01-06
Hey everyone, give a warm welcome to our newest members!
- @Ron Wood
- @Andrew Drob
- @Aamir Nayeem
- @Trọng Trương
- @Bill Clark
- @charlesz
Good to have you here =)
 5
52021-01-07
</wave>
Hey everyone, give a warm welcome to our newest members!
- @Connor Gervin
- @Patrick Jahns
- @AdoSa
- @G Byte
- @Advait Patel
Good to have you here =)
2021-01-08
Hey everyone, give a warm welcome to our newest members!
- @cole
- @Jeremy R
- @hrampur
- @Vincent Sheffer
- @Kamal Joshi
Good to have you here =)
 3
32021-01-09
Hey everyone, give a warm welcome to our newest members!
- @Coco
Good to have you here =)
 1
12021-01-10
Hey everyone, give a warm welcome to our newest members!
- @Moacy Barros
- @doanngocbao
Good to have you here =)
2021-01-11
Miss the old scaffolding from rails etc when building grpc go apps? – https://github.com/lileio/lile
Easily generate gRPC services in Go . Contribute to lileio/lile development by creating an account on GitHub.
Hey everyone, give a warm welcome to our newest members!
- @Nikita Kuprin
- @Bayrem Kaddoussi
- @Oleg Batozhnyi
Good to have you here =)
 2
22021-01-12
Hey everyone, give a warm welcome to our newest members!
- @Scott Cochran
- @JT
- @davejdyer
- @Kenji Nakamura
- @Liam Helmer
- @Ankit Rathi
- @Avishay Ashkenazi
- @Vesa
- @Dmitriy Solodukha
- @Leo D’Angelo
Good to have you here =)
 3
32021-01-13
Hey everyone, give a warm welcome to our newest members!
- @Gabin
- @Albert Attias
- @smaranankari.devops
- @RRR
- @Dennis Lipovsky
- @Tony Hirsch
- @Steve
Good to have you here =)
 3
32021-01-14
Hey everyone, give a warm welcome to our newest members!
- @Gokula Santhiya R
- @Thomas Hoefkens
- @Nikolay Iks
- @Hans Westerbeek
- @Lee Wilson
Good to have you here =)
 1
12021-01-15
Hey everyone, give a warm welcome to our newest members!
- @Qing Jiang
- @Sergei Kolobov
- @Pravin Singh Rajput
- @Michael Dizon
- @Oksana Chistaya
- @Justin Wehrman
- @Jon Jozwiak
- @Ashley Mooney
Good to have you here =)
 3
32021-01-16
Hey everyone, give a warm welcome to our newest members!
- @Jonas Sjödin
Good to have you here =)
 1
12021-01-17
Hey everyone, give a warm welcome to our newest members!
- @Zach M
- @S Bhaskar Sarma Emani
Good to have you here =)
 1
12021-01-18
Thank you for the welcome!
Hey everyone, give a warm welcome to our newest members!
- @Corey Smith
- @vamshisiddarth02
- @Nathan Flynn
- @Klaus F
- @Artyom Sukharev
Good to have you here =)
2021-01-19
Hey everyone, give a warm welcome to our newest members!
- @Zach Holt
- @Dahs81
Good to have you here =)
 1
1Thanks!
2021-01-20
Hey everyone, give a warm welcome to our newest members!
- @Dirk.Kappel
- @Chris Farnham
Good to have you here =)
 2
22021-01-21
Hey everyone, give a warm welcome to our newest members!
- @Mansoor Ebrahim
- @oskar
- @Srikar
- @Владимир Гуринович
- @rbadillo
- @Vladimir Mukhin
- @Ricardo Underwood
- @Moshe Edri
Good to have you here =)
 2
22021-01-22
Anyone using pritunl? Any feedback on this tool / the paid options?
I’m getting pushback from a client’s auditing team that Tailscale is not PCI compliant (still working through that with them). But just in case that doesn’t work out, I’m looking for real experience on pritunl. I feel like I’ve heard folks discuss it here before and weigh in on pros / cons, but can’t seem to find it.
i looked at pritunl some. or at least pritunl-zero, not the whole vpn. it just seems really confusing from the docs. and despite being open source and on github, issues are disabled, and there is basically a single contributor. didn’t give me a ton of confidence.
I have used pritunl multiple times, no experience with paid version though but community version is rock solid
Huh — can you use the community version with more than 1 server? Their pricing is a bit confusing, but it seems to limit community to 1 server from what I can see.
We had one server only
Gotcha
How many users are you planning to provision ?
30-50
We would need to go with the full paid option.
Okay got it, you can have one server and keep ami as standby
If something happens to server, you can create a new one from that AMI
@Erik Osterman (Cloud Posse) have you used pritunl with any Cloud Posse clients? I just saw you folks have a helmfile for it when searching through this Slack.
We’re just in the process of deploying it now, to replace our existing OpenVPN instances.
It’s a pretty great wrapper around OpenVPN & Wireguard from my experience, although, it’s effectively a one man operation (https://github.com/pritunl/pritunl/graphs/contributors) and the documentation leaves a lot to be desired.
Enterprise VPN server. Contribute to pritunl/pritunl development by creating an account on GitHub.
It’s still using Python v2, which leads to some deprecation warnings at present, but there is an effort via Zach to update the codebase to v3 (https://github.com/pritunl/pritunl/pull/468#issuecomment-689651018)
Ah good stuff Drew! That helps me in a couple aspects.
Thanks for weighing in folks — appreciate the thoughts / experience.
I can’t speak to it’s level of PCI compliance, however, since it’s just a wrapper around OpenVPN/Wireguard, the security vector shouldn’t be impacted to a great degree.
Sure thing, happy to provide some perspective. Feel free to DM me if you end up deciding on it, and if have any implementation questions.
Have you used the wireguard aspect of it at all? I would like to avoid any VPN configuration and wireguard seems superior in regards to be a mesh over point to point.
I’ve used it personally, but we’re not implementing it at present within my org. The thing about Pritunl though, is that you’ll have your users retrieve their configurations for either OpenVPN or Wireguard from the same web interface. After that, there really isn’t much maintenance for either OpenVPN or Wireguard.
The Electron-based Pritunl client (https://client.pritunl.com) sync’s any changes with your Pritunl cluster, so once users download their OpenVPN configuration, there really isn’t any ongoing end user maintenance.
By the way if you are on aws, there is. also aws managed openvpn called as aws-client-vpn that you can use, also supports OKTA integration
Thanks for that info Drew, that’s good to know about the maintenance of the two protocol configs + the client.
@aaratn I’ve implemented the AWS Client VPN for a client before… I wouldn’t go down that path again. VPN configurations are a nightmare to manage and AWS’s client VPN is super expensive for what it is.
This terraform module installs a client VPN. Contribute to masterpointio/terraform-aws-client-vpn development by creating an account on GitHub.
@Robert Horrox how’s pritunl holding up for your team?
once configured it has held up well, the okta integration has been very useful for our company. We are working on having the organization come from Okta so a user is placed into the correct Org on Pritunl to grant different levels of access. You can’t however push groups down from okta to pritunl
We have pritunl running on k8s and it has been stable. We also have it elsewhere on ec2 instances and it runs just fine there as well
Huh gotcha — How was setting up the cluster configuration? That hasn’t given you any trouble?
we don’t use a cluster per say on the k8s side
Yeah, that’s one of my problems with it right now… I don’t want to have to standup a cluster for a tool that I pay for.
I don’t know if it works with DocumentDB. By default, on kubernetes, we deploy mongodb as a container (it’s only for storing configuration data)
with ec2 instances I have mongodb atlas setup and once you do the initial setup all instances that connect to the cluster get their config from it
@Erik Osterman (Cloud Posse) would need to comment on trying to run multiple Pritunl pods inside k8s
Yea, so that works fine too. It’s basically deployed as a statefulset.
Requires though the enterprise version.
which is a “whopping” $600/year for unlimited seats and SSO.
(in otherwords dirt cheap)
they will charge you per-cluster
Yeah it’s super cheap… why are you evaluating alternatives @Erik Osterman (Cloud Posse) ?
I did do math on AWS VPN at one point, it gets expensive very fast
AWS VPN is crazy.
Lastly I would suggest looking at something like https://www.pomerium.io/ instead of a VPN. If you can get away without running a VPN, all the better. I don’t personally use pomerium, so buyer beware.

Pomerium is an identity-aware proxy that enables secure access to internal applications.
Hahah I think this is one of the most crowded spaces right now. Every flavor of BeyondCorp under the sun. That’s the first I’ve heard of this one.
That’s another cluster driven solution. I’m trying to avoid those if I can. But thanks for adding it to the pile.
what do you mean by “cluster driven”?
As in it has a centralized management layer that requires deploying a cluster for the solution to work. E.g. pritunl, Hashi Boundary, Pomerium, ect.
Really I think I’m just enamored with the simplicity of tailscale and now I don’t want anything else
heh, yeah, tailscale architecture is bomb. mesh private internet with acls. though i still want to self-host my own relays and coordination server
that cost per user though, 3 users is more than a pritunl license
sorry 5 users
i mean, comparing to pritunl pricing is a bit nuts. why it is so underpriced, i do not understand
Yeah maybe I would host the tailscale coordination server if I could.. That would solve the PCI compliance issues I’m running into. And I’m sure that’s lightweight anyway considering their Database was a JSON file up until recently.

When I first joined Tailscale, I was horrified to learn that “the database” was a single JSON file that was rewritten on any change. We migrated to something better.
Yeah, pritunl is definitely winning the pricing game 100%.
pritunl is just a simple wrapper around OpenVPN, in fact their whole codebase is opensource. Even the code that checks if you are an enterprise user
But compare pritunl vs tailscale vs strongDM… tailscale aint that bad.
we use StrongDM, their support is great. Product is a bit immature
i don’t think tailscale is even checking against licenses right now anyway ;)
Oh interesting… why do you use both?
in StrongDM you can give time grant access to users to databases
a VPN is needed for some items that SDM doesn’t support
Huh
similar to PCI, we have compliance requirements that keep us from public exposing endpoints
Hey everyone, give a warm welcome to our newest members!
- @Adam Schepis
- @Tim Bailey-Jones
- @iontom R
- @newbieCpo
- @Lawrence Lee
Good to have you here =)
2021-01-23
Hey everyone, give a warm welcome to our newest members!
- @Eyal Rot
Good to have you here =)
Hi all: ever want to learn more about raw Linux networking, e.g. under the Docker level? Here’s a very clear explanation of veth devices and bridging and the other machinery Docker/Kubernetes uses to route container packets to/from the network: https://iximiuz.com/en/posts/container-networking-is-simple/
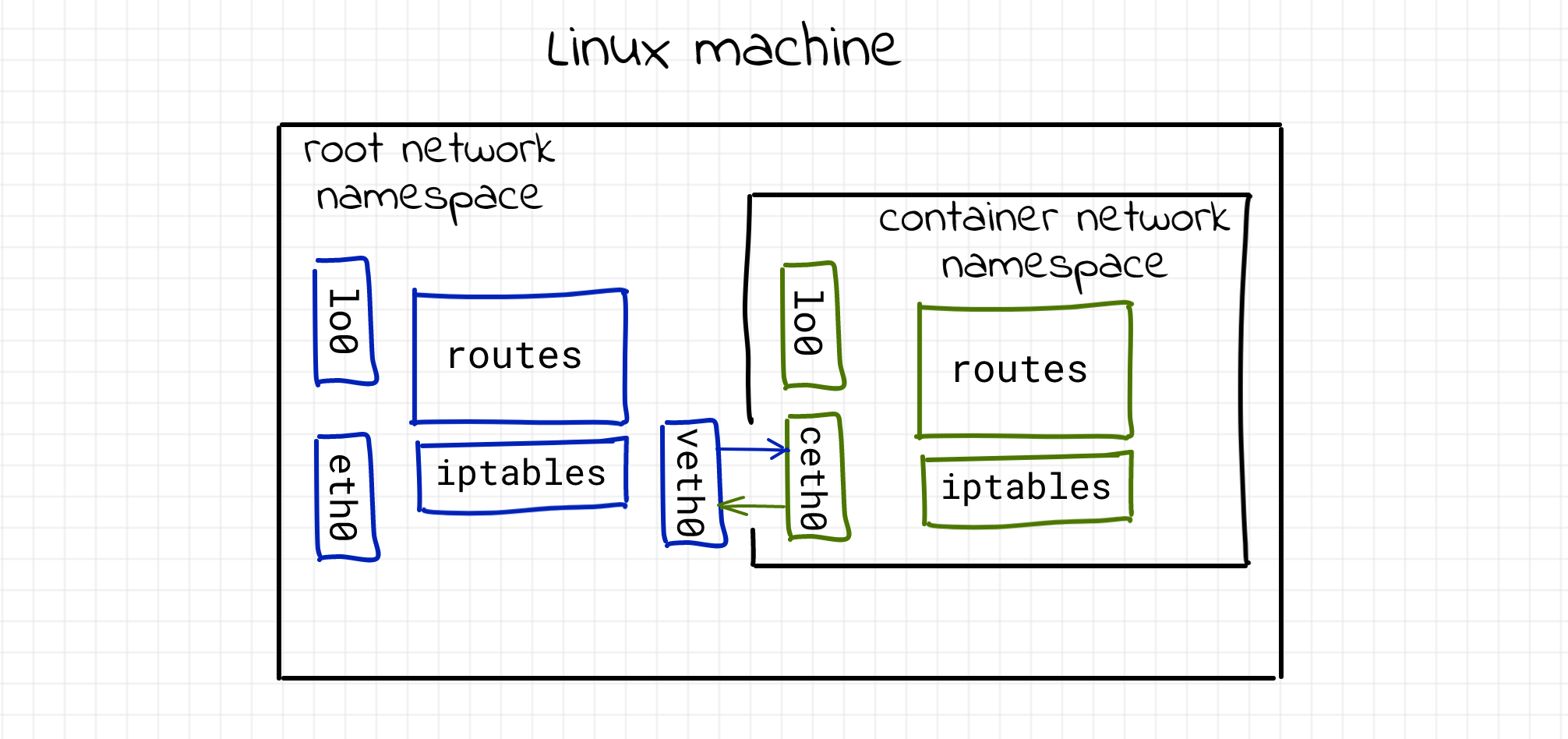
How container networking works under the hood? Setting up docker-like container networking from scratch. Bonus: podman rootless container networking explained.
2021-01-24
Hey everyone, give a warm welcome to our newest members!
- @markus011
- @Florian Kasper
Good to have you here =)
2021-01-25
Hey everyone, give a warm welcome to our newest members!
- @Greg Nicol
- @Doug Lane (he/him)
- @Michael Koroteev
- @Ofek Solomon
- @David Miranda
Good to have you here =)
 2
2thanks for the welcome
hey hey! glad you stopped by!
Hey all. I know atmos is still in progress, but I am curious about components directory missing. No terraform or helmfile in there. Or perhaps I have answered my own question?
Catalog of reusable Terraform components and blueprints for provisioning reference architectures - cloudposse/terraform-aws-components
Atmos is just a cli. Our components are kept in separate monorepo and versioned separately.
2021-01-26
Hey everyone, give a warm welcome to our newest members!
- @Chris Anderla
- @johnpc
- @Pedro Antonio Bratti
- @Jeremy Rauch
- @contact531
- @Madan Kapoor
Good to have you here =)
 5
52021-01-27
Hey everyone, give a warm welcome to our newest members!
- @Saurabh Hirani
- @Philip Asiala
- @Jerrod Finn
- @Thomas Picquet
- @Mahmoud
Good to have you here =)
2021-01-28
Hi all, thanks for all you’re doing to help the community. I joined the office-hours yesterday and it was quite interesting. I work on a small internal tools team and I’m trying to really focus on Devops and IaC to mature our processes. I’ve been looking into terraform / terragrunt all week and I’ve noticed something that feels strange to me that seems to be considered best practice across a number of tools and I was hoping to get some input from all of you.
I may get some of the wording wrong here but I’ll try my best to be descriptive. So it seems that it’s common to split things up into modules that do individual jobs, and environments which control configuration values and compositional instructions. The combination of configs and compositional work flows in the environments seems odd to me. I can see a place for having some of it in cases where you’d want them to have some different structure (maybe you want some kind of chaos service in staging but not in prod for example), but generally it would seem like you’d want to have most of your composition to be shared between environments. To make an analogy to software development that I’m more used to, we would create a feature branch, and work on it, then merge that code to staging, after it was tested there the same code would be merged to a prod branch which would deploy to prod. You’d have different settings for each env but the code would be the same. I wouldn’t create a prod and staging directory in my source and try to copy my staging code to prod when I was ready for it to be deployed.
Where does this practice come from? Is there any argument against doing it? Does anyone know of any example repositories that do handle most of the composition in a shared folder and only uses prod and staging for things that would make them different? I’m mainly focused on terragrunt right now since I’m new and it seems to be a mature system with plenty of users and help but any examples would help.
The files that live in the prod and staging folder are typically very small. They reference different versions of a “module” so that you can do exactly what you are talking about up above.
But it’s also not the only way to do it. My team doesn’t do it that way, they do it in a more typical app-dev kind of way. There’s lots of different ways to skin this particular cat
Take a look at #atlantis for a tool that is popular around here that helps a lot when deploying IaC
CP does it with GitHub actions as well, though I think that process is more homegrown and “proprietary”? Not sure how extensible it is.
Then others use Terraform Cloud with nice success
so, one way to do it might to be to call a shared “module” that actually handles most of the composition?
yes, and utilizing different versions of that module let you gradually promote something up through your environments
while sharing the same codebase
that module would be called from each of the environments but with different inputs
yes
that makes a lot of sense
thanks a bunch for the tips
also see https://www.youtube.com/watch?v=4MLBpBqZmpM. It’s a whole office hours about different Terraform cloud services
@Evan Pitstick happy to talk about this again on #office-hours
in the next 1-2 months, we’ll have more documentation on getting started with our reference architecture. in the next week, we’ll have documentation for our various components coming out. after that we’re focused on archiving a lot of our legacy documentation before starting down the path of documenting our current approach.
@Evan Pitstick I’m also interested in this, how to map code releases to production/environment releases. I’ll be curious to be on the Office Hours this week!
Hey everyone, give a warm welcome to our newest members!
- @Evan Pitstick
- @Brad McCoy
- @Ratko Nikolovski
- @imran hussain
Good to have you here =)
2021-01-29
Hey everyone, give a warm welcome to our newest members!
- @Jordan Mendler
- @Stas Efremov
- @Iurii
- @risto78
- @kien241
- @Nathaniel Selzer
- @Lionel LONKAP
- @Joe Herman
Good to have you here =)
 6
6Hey @Jordan Mendler! welcome
2021-01-30
Hey everyone, give a warm welcome to our newest members!
- @Sergio (Cloud Posse)
- @Sarath Pantala
- @Alex Montgomery
Good to have you here =)
 3
3

