#office-hours (2022-04)
“Office Hours” are every Wednesday at 11:30 PST via Zoom. It’s open to everyone. Ask questions related to DevOps & Cloud and get answers! https://cloudposse.com/office-hours
Public “Office Hours” are held every Wednesday at 11:30 PST via Zoom. It’s open to everyone. Ask questions related to DevOps & Cloud and get answers!
https://cpco.io/slack-office-hours
Meeting password: sweetops
2022-04-06
Wanted to share this for office hours today. Its a pretty nifty tool that I’ve been putting to use lately. Its already helped me shave a couple dozen $$/mo off of a AWS account which will add up to hundreds/thousands by year end. https://www.infracost.io/ https://github.com/infracost/infracost

Infracost helps engineers see cloud costs before launching resources. Map costs to code directly in pull requests. Take action directly in your workflow.
Cloud cost estimates for Terraform in pull requests Love your cloud bill!

Hear from David Trejo, a member of Chime’s Security Engineering Team, how he and the team created a proactive security culture at Chime
Looks interesting

Hear from David Trejo, a member of Chime’s Security Engineering Team, how he and the team created a proactive security culture at Chime
Is monocle open source?
@here office hours is starting in 30 minutes! Remember to post your questions here.
new member here  . what is an office hour?
. what is an office hour?
it’s a live session that we do - open mic, Q&A. usually about 30 people on the call.
happens every wednesday
Erik Osterman (Cloud Posse) has joined Public “Office Hours”
Christopher Picht has joined Public “Office Hours”
Emile Fugulin has joined Public “Office Hours”
dario erregue has joined Public “Office Hours”
David Hawthorne has joined Public “Office Hours”
Michael Jenkins has joined Public “Office Hours”
Mazin Ahmed has joined Public “Office Hours”
Vlad Ionescu has joined Public “Office Hours”
Isa Aguilar has joined Public “Office Hours”
deniz gokcin has joined Public “Office Hours”
Mazin Ahmed has joined Public “Office Hours”
Mohammed Yahya has joined Public “Office Hours”
dag viggo lokoeen has joined Public “Office Hours”
Jim Park has joined Public “Office Hours”
Yusuf has joined Public “Office Hours”
Matt Calhoun has joined Public “Office Hours”
Connor High has joined Public “Office Hours”
Connor High has joined Public “Office Hours”
Matt Gowie has joined Public “Office Hours”
Tim Gourley has joined Public “Office Hours”
Ben Smith (Cloud Posse) has joined Public “Office Hours”
Jim C has joined Public “Office Hours”
Jeremy (Cloud Posse) has joined Public “Office Hours”
Kris Musard has joined Public “Office Hours”
Sherif Abdel-Naby has joined Public “Office Hours”
stelios L has joined Public “Office Hours”
Tim Gourley has joined Public “Office Hours”
Vicken Simonian has joined Public “Office Hours”
Abraham Quintero has joined Public “Office Hours”
Allen Lyons has joined Public “Office Hours”
Ralf Pieper has joined Public “Office Hours”
Ross Rfd has joined Public “Office Hours”
GitHub Action for Infracost. Shows cloud cost estimates for Terraform in pull requests.
er… rather https://github.com/infracost/actions/
GitHub Action for Infracost. Shows cloud cost estimates for Terraform in pull requests.

Infracost is an official HashiCorp partner. We work together to ensure that Infracost can be used alongside Terraform Cloud and integrated into your workflow.
Amer Zec has joined Public “Office Hours”
wasim k has joined Public “Office Hours”
AWS also have a 100k dollar bill for a single click of a button :D https://www.cyclic.sh/posts/aws-s3-why-sometimes-you-should-press-the-100k-dollar-button
dag viggo lokoeen has joined Public “Office Hours”
Find credentials all over the place
Jose Figueredo has joined Public “Office Hours”

The Amazon Elastic Kubernetes Service (Amazon EKS) team is pleased to announce support for Kubernetes 1.22. Amazon EKS, Amazon EKS Distro, and Amazon EKS Anywhere can now run Kubernetes version 1.22. The upstream project theme for this release is “Reaching New Peaks.” The theme for the release, according to release lead Savitha Raghunathan, is due to what she […]
Anyone going to KubeCon EU 2022 ? 
Before you begin You must use a kubectl version that is within one minor version difference of your cluster. For example, a v1.23 client can communicate with v1.22, v1.23, and v1.24 control planes. Using the latest compatible version of kubectl helps avoid unforeseen issues. Install kubectl on Windows The following methods exist for installing kubectl on Windows: Install kubectl binary with curl on Windows Install on Windows using Chocolatey or Scoop Install kubectl binary with curl on Windows Download the latest release v1.
Kubernetes version 1.18 on Amazon EKS will no longer be supported on March 31st, 2022. On this day, you will no longer be able to create new 1.18 clusters. Existing 1.18 clusters will be automatically updated by Amazon EKS to the latest available platform version of Kubernetes version 1.19 through a gradual deployment process after the end of support date.
We recommend you upgrade existing 1.18 clusters and worker nodes to at least 1.19 as soon as practical.
Learn more:
Introduction IT Industry research, such as Accelerate, shows improving a company’s ability to deliver software is critical to their overall success. The following key practices and design principles are cornerstones to that improvement. Version control of code and configuration Automation of Deploy…
wasim k has joined Public “Office Hours”
Tooling for kubernetes.slack.com
deniz gokcin has joined Public “Office Hours”
https://github.com/kube-rs/kube-rs https://github.com/linkerd/linkerd2/tree/main/policy-controller Last is linkerd new policy controller using kube-rs, can be a good inspiration
2022-04-07
2022-04-08
Question for next office-hours — How have folks automated AWS IAM Access Key + Secret Key rotation policies (e.g. IAM keys are only active for 1 year)? I’ve always thought about doing it, but never went down the rabbit hole. Huge bonus points if somebody has a simple solution that doesn’t involve lambda
Are you talking for IAM users or for CI/CD automation? If the latter I don’t use them at all
IAM users is what I’m thinking about.
Though I would like to it for service accounts as well. I have a client who is using IAM service account users for CircleCI.
I actually use SSO for users and then for my CI/CD as I use GitHub actions I actually use OIDC and grant roles so in both cases I’m using STS credentials that are short lived
Alternatively use Hashicorp Vault to hand out dynamic credentials
using an Access Key/Secret Key is my last resort for precisely this reason
Well, I thought lambda WAS the easy way . That being said, if you want more fine-grained control over the timing you could throw up a cron job on a VM somewhere. Caveat being that you’d end up having to use a service account to auto-rotate the keys, which in turn would need keys, and would quickly turn into key rotation inception. I threw up my own OIDC solution that rotates JWKS at a set interval using cron. It’s a headache for sure… Vault may have this functionality? Not sure, I have only used it a handful of times.
Vault could definitely handle it… just setup the AWS credentials and then request them from Vault and get temporary access just like any other Vault lease.
2022-04-11
2022-04-12

Lenses for your DataOps enterprise platform, to operate with confidence on Apache Kafka with intuitive ui and fine-grained controls
Aiven’s fully managed, open source cloud data platform lets you create the data pipelines you always dreamed of – in under 10 minutes. On all major clouds everywhere.

You can now upgrade your PostgreSQL and SQL Server instances in-place to the latest major version.
My life just got better
2022-04-13
Question for today: Pros and cons of using the latest EKS AMIs or managing roll-out of new AMI releases manually.
@here office hours is starting in 30 minutes! Remember to post your questions here.
hmm I do have a question that maybe is out of scope for office hours, if so feel free to not answer or just point me in the right direction, but are there any examples on the use of helmfile that showcase how one might use it in a “bigger” situation? I.E, multiple releases spanning 1-2 env’s that maybe pulls from a helm repo and overrides some of those values as well. Maybe it’s just a complete misunderstanding on my part but I was finding the examples in the helmfile repo kind-of lackluster, and a lot of the guides I came across on the internet pretty much showcased an entirely different way of doing it.. Not sure if there’s a “standard” or just kind of the wild west lol. Also, I guess a followup would be, if I decide to just roll with Argocd and Gitops is helmfile still relevant in that regard? It seems like a pretty lightweight wrapper overall but due to complete noobness I can’t be sure they’re compatible.
Lol I guess my particular situation is that I’ve learned how to install helm charts from a repo, and can make one from scratch, but somehow am scratching my head on how to create a repeatable CI\CD pipeline in which I can say “I need istio, these are the values I need you to overwrite, please do the thing”
My first office hours, so apologies if this isn’t the place
another question for today: what kind of a git repo structure do you recommend if I want to seperate my terraform modules in repository A along with the terragrunt files for some common resources like the vpc, alb some security groups etc. and store my app source code and app specific terragrunt files in repository B(ecr, ecs, app security groups etc.) I also want to note that my ecs hcl file needs dependencies from the common resources(like vpc id)
deniz gokcin has joined Public “Office Hours”
Erik Osterman (Cloud Posse) has joined Public “Office Hours”
Brian Pauley has joined Public “Office Hours”
Marcos Soutullo has joined Public “Office Hours”
MALCON MOREIRA has joined Public “Office Hours”
Christopher Picht has joined Public “Office Hours”
dag viggo lokoeen has joined Public “Office Hours”
Eric Berg has joined Public “Office Hours”
Jim Park has joined Public “Office Hours”
Arthur Dent has joined Public “Office Hours”
Andy Roth has joined Public “Office Hours”
Vlad Ionescu has joined Public “Office Hours”
Jesus Martinez has joined Public “Office Hours”
Oliver Schoenborn has joined Public “Office Hours”
Matt Calhoun has joined Public “Office Hours”
Scott Mathson has joined Public “Office Hours”
Michael Jenkins has joined Public “Office Hours”
Stevan Arychuk has joined Public “Office Hours”
Tim Gourley has joined Public “Office Hours”
Brandon James Miller has joined Public “Office Hours”
Jeremy (Cloud Posse) has joined Public “Office Hours”
Jose Figueredo has joined Public “Office Hours”
Mazin Ahmed has joined Public “Office Hours”
Josh B has joined Public “Office Hours”
dag viggo lokoeen has joined Public “Office Hours”
Waqar Ahmed has joined Public “Office Hours”
Marcelo Santoro has joined Public “Office Hours”
Connor High has joined Public “Office Hours”
Jeremy Bouse has joined Public “Office Hours”
Isa Aguilar has joined Public “Office Hours”
Connor High has joined Public “Office Hours”
Paul Bullock has joined Public “Office Hours”
Jose Figueredo has joined Public “Office Hours”
Marin Purgar has joined Public “Office Hours”
Guilherme Borges has joined Public “Office Hours”
Shaun Wang has joined Public “Office Hours”
Allen Lyons has joined Public “Office Hours”
michael dizon has joined Public “Office Hours”
Josh B has joined Public “Office Hours”
Community Note
• Please vote on this issue by adding a :+1: reaction to the original issue to help the community and maintainers prioritize this request • Please do not leave “+1” or other comments that do not add relevant new information or questions, they generate extra noise for issue followers and do not help prioritize the request • If you are interested in working on this issue or have submitted a pull request, please leave a comment
Update from HashiCorp, 2022-02-25
Hi everyone,
In light of how much traction this issue has gained, and the amount of information contained within, @joe-a-t has graciously allowed us to make edits to the description of this GitHub Issue to better reflect its current state, and so that we may pin it to make it more visible. We would like to sincerely thank him for the opportunity to do so. For the sake of transparency, and to not lose any context, the original issue description and title will be retained beneath this update.
Breakdown
On 2022-02-10, the AWS Provider team at HashiCorp released a new major version of the AWS Provider for Terraform (v4.0.0), which included breaking changes to the aws_s3_bucket resource. The update introduced several independent aws_s3_bucket_* resources to manipulate the configuration of S3 buckets, where these configuration options previously were arguments to the aws_s3_bucket resource itself. This issue spawned out of that change, has received quite a bit of valuable feedback, and is being used as a centralized meeting point for ongoing discussions around these changes.
Information around these changes may be found:
• Upcoming changes in Version 4.0 of the AWS Provider • Terraform AWS Provider 4.0 Refactors S3 Bucket Resource (blog post) • Terraform AWS Provider Version 4 Upgrade Guide
Action Items
Given the amount of feedback that we received after the release, the AWS Provider team has been following this issue (as well as any other avenues of feedback we can find) and taking steps to try to alleviate some of the burden placed on operators with this release. The team continues to investigate additional avenues, and will continue to update this issue with additional information where possible. These efforts include:
Completed
• A clarifying comment on what decisions were made, and why they were made • An update to the aforementioned blog post to provide more clarification around how resource configuration has changed (namely with regards to configurable -> read-only/computed arguments • A clarifying comment on when imports are needed and an accompanying update to the migration guide
Currently Investigating
-
Tooling to help with configuration migration
We are currently investigating potential tooling options to help operators migrate from legacy
aws_s3_bucketresources to the newaws_s3_bucket_*resources. We have identified potential existing tooling and have reached out to the owner of the tool to try to help coordinate efforts to make the tool robust enough to share publicly. This is still in the early phases, so the information we can share on it is relatively limited. Despite this, we feel it’s appropriate to share that we are looking into it, given the large amount of community interest. -
Marking deprecated arguments as optional in AWS Provider
v4.xThis change aims at splitting the difference between the behavior in
v3.xandv4.xby marking deprecated arguments as optional. The goal here is to allow operators more time to transition before the deprecated arguments are fully removed inv5.x. Optional arguments would display deprecation warnings, but would not prevent Terraform from running, as was the behavior with the initialv4.xreleases. Documentation will be written in order to provide as much clarity as possible around how to cope with these changes within configurations. -
Backporting
aws_s3_bucket_*resources to AWS Providerv3.xThis change aims to bring the new
aws_s3_bucket_*resources into thev3.xseries of releases in order to give operators more time to plan and execute migration to the new resources without needing to make the jump tov4.x. This would allow operators to useaws_s3_bucketresources alongside the newaws_s3_bucket_*resources, configuring buckets and updating configurations to the new standards as they see fit, without worry of deprecation notices or failed Terraform operationsGiven that backporting resources in this way falls outside of our normal processes, we would like to be explicit around expectations. Bugs in distinct
aws_s3_bucket_*resources will be backported to ensure functionality, but additional features will not be backported. Documentation will be updated as well to ensure that this expectation is clearly communicated.
Original issue information
Title: Change the S3 bucket refactor to be a new resource instead of modifying the existing one
Description
Do not change the existing aws_s3_bucket resource in v4 and instead provide a new aws_s3_minimal_bucket or similar resource that people can use if they want your changes to split out various settings into stand alone resources.
My company has literally thousands of AWS buckets configured through Terraform from hundreds of different root modules. Having to run separate terraform import commands for all of the settings you split out into separate resources per your upgrade instructions in https://registry.terraform.io/providers/hashicorp/aws/latest/docs/guides/version-4-upgrade#s3-bucket-refactor is quite frankly an insane demand to make for users.
Right now, our only options appear to be:
- Pin to v3 permanently and miss out on all future enhancements/bugfixes/features that the AWS provider publishes.
- Spend countless hours running (or making our own tool to run) thousands of
terraform importcommands in hundreds of Terraform directories.
Please reconsider this change immediately or at least provide tooling to ease adoption.
New or Affected Resource(s)
• aws_s3_bucket
Potential Terraform Configuration References
• #0000
Update 2/22/2022
FYI, I (@joe-a-t) chatted with HashiCorp separately and gave them permission to update the issue (including the title and this comment) if they would like the issue to more accurately reflect the work that they are planning on doing.
@managedkaos
Community Note
• Please vote on this issue by adding a :+1: reaction to the original issue to help the community and maintainers prioritize this request • Please do not leave “+1” or other comments that do not add relevant new information or questions, they generate extra noise for issue followers and do not help prioritize the request • If you are interested in working on this issue or have submitted a pull request, please leave a comment
Update from HashiCorp, 2022-02-25
Hi everyone,
In light of how much traction this issue has gained, and the amount of information contained within, @joe-a-t has graciously allowed us to make edits to the description of this GitHub Issue to better reflect its current state, and so that we may pin it to make it more visible. We would like to sincerely thank him for the opportunity to do so. For the sake of transparency, and to not lose any context, the original issue description and title will be retained beneath this update.
Breakdown
On 2022-02-10, the AWS Provider team at HashiCorp released a new major version of the AWS Provider for Terraform (v4.0.0), which included breaking changes to the aws_s3_bucket resource. The update introduced several independent aws_s3_bucket_* resources to manipulate the configuration of S3 buckets, where these configuration options previously were arguments to the aws_s3_bucket resource itself. This issue spawned out of that change, has received quite a bit of valuable feedback, and is being used as a centralized meeting point for ongoing discussions around these changes.
Information around these changes may be found:
• Upcoming changes in Version 4.0 of the AWS Provider • Terraform AWS Provider 4.0 Refactors S3 Bucket Resource (blog post) • Terraform AWS Provider Version 4 Upgrade Guide
Action Items
Given the amount of feedback that we received after the release, the AWS Provider team has been following this issue (as well as any other avenues of feedback we can find) and taking steps to try to alleviate some of the burden placed on operators with this release. The team continues to investigate additional avenues, and will continue to update this issue with additional information where possible. These efforts include:
Completed
• A clarifying comment on what decisions were made, and why they were made • An update to the aforementioned blog post to provide more clarification around how resource configuration has changed (namely with regards to configurable -> read-only/computed arguments • A clarifying comment on when imports are needed and an accompanying update to the migration guide
Currently Investigating
-
Tooling to help with configuration migration
We are currently investigating potential tooling options to help operators migrate from legacy
aws_s3_bucketresources to the newaws_s3_bucket_*resources. We have identified potential existing tooling and have reached out to the owner of the tool to try to help coordinate efforts to make the tool robust enough to share publicly. This is still in the early phases, so the information we can share on it is relatively limited. Despite this, we feel it’s appropriate to share that we are looking into it, given the large amount of community interest. -
Marking deprecated arguments as optional in AWS Provider
v4.xThis change aims at splitting the difference between the behavior in
v3.xandv4.xby marking deprecated arguments as optional. The goal here is to allow operators more time to transition before the deprecated arguments are fully removed inv5.x. Optional arguments would display deprecation warnings, but would not prevent Terraform from running, as was the behavior with the initialv4.xreleases. Documentation will be written in order to provide as much clarity as possible around how to cope with these changes within configurations. -
Backporting
aws_s3_bucket_*resources to AWS Providerv3.xThis change aims to bring the new
aws_s3_bucket_*resources into thev3.xseries of releases in order to give operators more time to plan and execute migration to the new resources without needing to make the jump tov4.x. This would allow operators to useaws_s3_bucketresources alongside the newaws_s3_bucket_*resources, configuring buckets and updating configurations to the new standards as they see fit, without worry of deprecation notices or failed Terraform operationsGiven that backporting resources in this way falls outside of our normal processes, we would like to be explicit around expectations. Bugs in distinct
aws_s3_bucket_*resources will be backported to ensure functionality, but additional features will not be backported. Documentation will be updated as well to ensure that this expectation is clearly communicated.
Original issue information
Title: Change the S3 bucket refactor to be a new resource instead of modifying the existing one
Description
Do not change the existing aws_s3_bucket resource in v4 and instead provide a new aws_s3_minimal_bucket or similar resource that people can use if they want your changes to split out various settings into stand alone resources.
My company has literally thousands of AWS buckets configured through Terraform from hundreds of different root modules. Having to run separate terraform import commands for all of the settings you split out into separate resources per your upgrade instructions in https://registry.terraform.io/providers/hashicorp/aws/latest/docs/guides/version-4-upgrade#s3-bucket-refactor is quite frankly an insane demand to make for users.
Right now, our only options appear to be:
- Pin to v3 permanently and miss out on all future enhancements/bugfixes/features that the AWS provider publishes.
- Spend countless hours running (or making our own tool to run) thousands of
terraform importcommands in hundreds of Terraform directories.
Please reconsider this change immediately or at least provide tooling to ease adoption.
New or Affected Resource(s)
• aws_s3_bucket
Potential Terraform Configuration References
• #0000
Update 2/22/2022
FYI, I (@joe-a-t) chatted with HashiCorp separately and gave them permission to update the issue (including the title and this comment) if they would like the issue to more accurately reflect the work that they are planning on doing.
Kris Musard has joined Public “Office Hours”
shreenu kumar has joined Public “Office Hours”
Nimesh Amin has joined Public “Office Hours”
wasim k has joined Public “Office Hours”
Amer Zec has joined Public “Office Hours”
Ross Rfd has joined Public “Office Hours”
2022-04-14
As requested, here’s the link to the Containers from the Couch livestream I’ll be doing later: https://twitter.com/rothgar/status/1514627176804470787
2022-04-15
2022-04-20
@here office hours is starting in 30 minutes! Remember to post your questions here.
due to many announcements, there was no time for Q&A last week. will you answer questions from last week?
Yep, and we have yours on the list from last week
Arthur Dent has joined Public “Office Hours”
Andy Miguel (Cloud Posse) has joined Public “Office Hours”
venkata mutyala has joined Public “Office Hours”
Andy Roth has joined Public “Office Hours”
Erik Osterman (Cloud Posse) has joined Public “Office Hours”
Emile Fugulin has joined Public “Office Hours”
Vlad Ionescu has joined Public “Office Hours”
Igor Miltchman has joined Public “Office Hours”
Isa Aguilar has joined Public “Office Hours”
Brian Pauley has joined Public “Office Hours”
Brandon James Miller has joined Public “Office Hours”
Matt Calhoun has joined Public “Office Hours”
Derek Davis has joined Public “Office Hours”
deniz gokcin has joined Public “Office Hours”
Tim Gourley has joined Public “Office Hours”
Jim Park has joined Public “Office Hours”
Matt Gowie has joined Public “Office Hours”
Josh B has joined Public “Office Hours”
Steven Hopkins (Cloud Posse) has joined Public “Office Hours”
Kris Musard has joined Public “Office Hours”
Eric Berg has joined Public “Office Hours”
dag viggo lokoeen has joined Public “Office Hours”
links from today’s session
• https://github.com/hashicorp/terraform/issues/19898#issuecomment-1101853833
• https://thehackernews.com/2022/04/github-says-hackers-breach-dozens-of.html
• https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/pricing_product
• https://calebporzio.com/i-just-hit-dollar-100000yr-on-github-sponsors-heres-how-i-did-it
• https://aws.amazon.com/about-aws/whats-new/2022/04/aws-single-sign-on-hipaa-eligible/
• https://blog.symops.com/2022/04/14/terraform-pipeline-with-github-actions-and-github-oidc-for-aws/
Jose Figueredo has joined Public “Office Hours”
Oliver Schoenborn has joined Public “Office Hours”
Yusuf has joined Public “Office Hours”
Ayobami Bamigboye has joined Public “Office Hours”
Stevan Arychuk has joined Public “Office Hours”
Scott Mathson has joined Public “Office Hours”
Marc Tamsky has joined Public “Office Hours”
Christopher Picht has joined Public “Office Hours”
Alexandr Vorona has joined Public “Office Hours”
Michael Jenkins has joined Public “Office Hours”
Andrew Vitko has joined Public “Office Hours”
Connor High has joined Public “Office Hours”
Here’s JHipster’s page on the bug bounty stuff they do: https://www.jhipster.tech/bug-bounties/
Jim C has joined Public “Office Hours”
Ayobami Bamigboye has joined Public “Office Hours”
Steven Hopkins (Cloud Posse) has joined Public “Office Hours”
Florain Drescher has joined Public “Office Hours”
Paul Bullock has joined Public “Office Hours”
Jim C has joined Public “Office Hours”
Mohammed Almusaddar has joined Public “Office Hours”
emem emem has joined Public “Office Hours”
Declaratively install and manage multiple Helm chart releases
Find outdated or deprecated Helm charts running in your cluster.
Get your resource requests “Just Right”
2022-04-21
2022-04-27
@here office hours is starting in 30 minutes! Remember to post your questions here.
Andy Miguel (Cloud Posse) has joined Public “Office Hours”
Vlad Ionescu has joined Public “Office Hours”
Christopher Picht has joined Public “Office Hours”
Andrew Elkins has joined Public “Office Hours”
Allan Mohr has joined Public “Office Hours”
Isa Aguilar has joined Public “Office Hours”
Eric Berg has joined Public “Office Hours”
David Hawthorne has joined Public “Office Hours”
Guilherme Borges has joined Public “Office Hours”
Emile Fugulin has joined Public “Office Hours”
dag viggo lokoeen has joined Public “Office Hours”
Opinions and thoughts on K8s ingress controllers for high volume deployments.
• traefik (currently using)
• haproxy (currently considering)
• nginx
• ??
Running in to some scaling issues when under heavy load. It’s possible that traefik needs further configuration
Curious what the community thinks is the best option or what options should we be investigating.
Where is this running? AWS, GCP, Azure, on-prem?
AWS and Azure. Own k8s cluster on AWS. Main pain point is on deploy
(on a tangential note, https://www.vladionescu.me/posts/scaling-containers-on-aws-in-2022/)
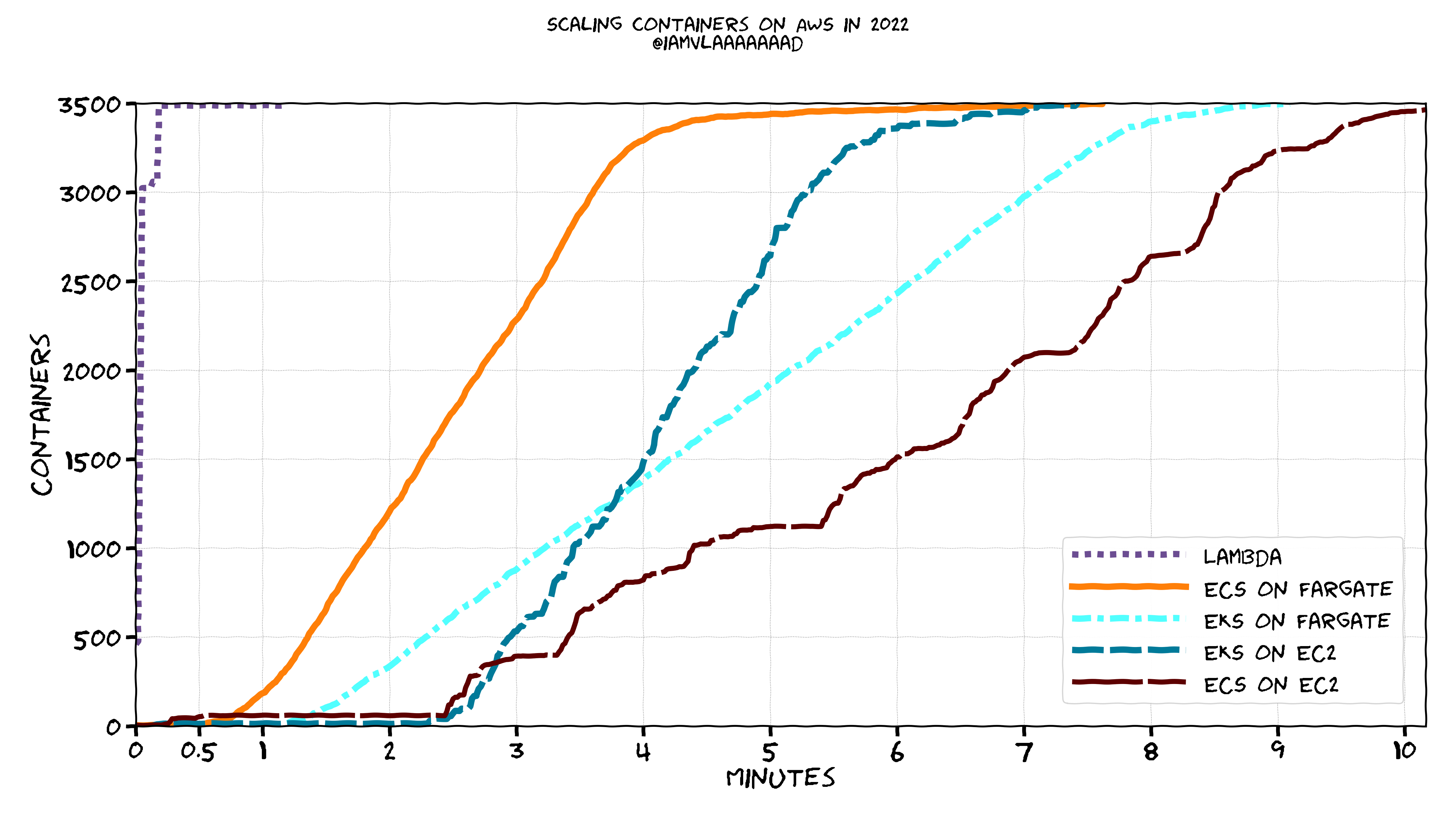
Comparing how fast containers scale up in 2022 using different orchestrators on AWS
nginx-ingress open source version is abysmal for large deployments as adding/removing pods causes a SIGHUP
IMO you should go straight to the amazon load balancer controller and work with AWS who can help with any performance issues.
Can you also elaborate on what qualifies as
high volume deployments
@Andrew Elkins https://www.youtube.com/watch?v=ZTrPtknU2KA&t=2063s
Andy Roth has joined Public “Office Hours”
Matt Calhoun has joined Public “Office Hours”
Connor High has joined Public “Office Hours”
Erik Osterman (Cloud Posse) has joined Public “Office Hours”
Paul Bullock has joined Public “Office Hours”
Josh B has joined Public “Office Hours”
Brandon Miller has joined Public “Office Hours”
Alex Kiss has joined Public “Office Hours”
Isaac M has joined Public “Office Hours”
What advice do you have for how to communicate expectations when people decide to use something brand new that is still super beta/rough, are having problems, and are annoyed that things aren’t working?
I’d re-iterate that problems arising from beta products they decide to move forward with that THEY own supporting/troubleshooting them/care and feeding. I wouldn’t roadblock them though.
It depends… who are the people? What is it they’re using?
Lucas Andrade has joined Public “Office Hours”
Tim Gourley has joined Public “Office Hours”
Benjamin Smith has joined Public “Office Hours”
Ralf Pieper has joined Public “Office Hours”
links from today’s session
• https://github.blog/changelog/2022-04-25-git-io-deprecation/
• https://github.com/cloudposse/build-harness/issues/314
• https://www.theregister.com/AMP/2022/04/20/aws_log4j_patches/
• https://github.com/FairwindsOps/reckoner
• https://medium.com/@cfatechblog/edge-computing-at-chick-fil-a-7d67242675e2
Josh B has joined Public “Office Hours”
Vlad Ionescu has joined Public “Office Hours”
PePe Amengual has joined Public “Office Hours”
looks like is similar to what this does https://github.com/apparentlymart/terraform-aws-tf-registry
Terraform module for creating a simple private Terraform registry in AWS with DynamoDB
Ross Rfd has joined Public “Office Hours”
Arthur Dent has joined Public “Office Hours”
Brian Pauley has joined Public “Office Hours”
Tony Scott has joined Public “Office Hours”
Matt Gowie has joined Public “Office Hours”
dag viggo lokoeen has joined Public “Office Hours”
Justin Davis has joined Public “Office Hours”
Florain Drescher has joined Public “Office Hours”
Nimesh Amin has joined Public “Office Hours”
Michael Jenkins has joined Public “Office Hours”
resource "awsutils_expiring_iam_access_key" "default" {
count = module.this.enabled && local.create_expiring_access_key ? 1 : 0
user = local.username
max_age = var.iam_access_key_max_age
}
Andrew Thompson has joined Public “Office Hours”
Amer Zec has joined Public “Office Hours”
dag viggo lokoeen has joined Public “Office Hours”
Express inspired web framework written in Go
2022-04-28
https://css-tricks.com/making-mermaid-diagrams-in-markdown/
https://github.blog/2022-02-14-include-diagrams-markdown-files-mermaid/#<i class="em em-~"</i>text=Mermaid%20has%20been%20getting%20increasingly,feature%20to%20everyone%20on%20GitHub>.
In reference to the question asked yesterday about how to keep expectations realistic during OSS development… I was reading this and it seems like a great solution. Essentially use Mermaid to maintain a roadmap within your readme. First link shows an example roadmap, while the second is the Github-specific implementation details from their announcement post. Haven’t done this yet myself, so I can’t say with 100% certainty that it will be painless but it does seem to be possible :)

While Mermaid diagrams are not Markdown-exclusive, they is Markdown-inspired. using the same markup abstractions.
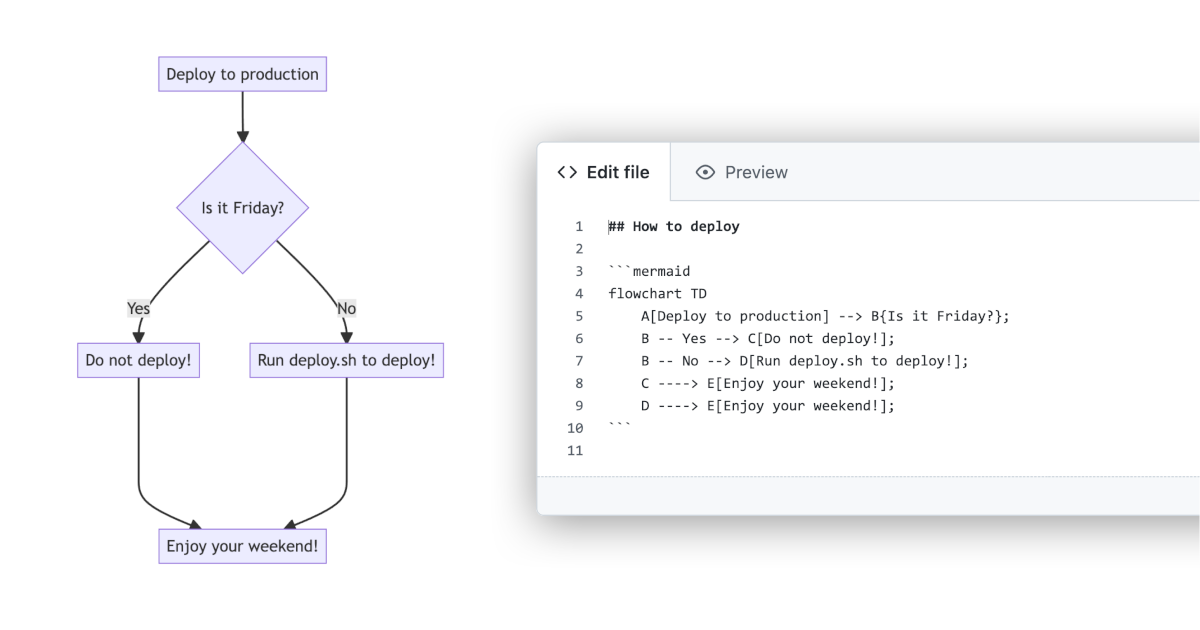
Mermaid is a JavaScript based diagramming and charting tool that takes Markdown-inspired text definitions and creates diagrams dynamically in the browser.
