#random (2024-06)
Non-work banter and water cooler conversation
A place for non-work-related flimflam, faffing, hodge-podge or jibber-jabber you’d prefer to keep out of more focused work-related channels.
Archive: https://archive.sweetops.com/random/
2024-06-04
Hi everyone. Today join a new DevOpsDays Ukraine: Let’s Talk Security edition on June 4-5!
During two days dedicated to DevSecOps 13 speakers will share presentations and insightful ignites on creating an action plan and building security measures into every stage of development.
Learn how to integrate security as a shared responsibility throughout the entire IT lifecycle. Register: https://devopsdays.com.ua/

Let’s Talk Security conference by DevOpsDays Ukraine community. We’ll discuss context-based security, cloud hacking scenarios, cyberattacks and the complexities of cyber warfare, vulnerability management implementation with AWS and more. Participation is free! See you on June 4-5!
2024-06-06
The NixOS Foundation board
announced on April 30 that Eelco Dolstra is stepping down from the board following the recent calls for his resignation.
Eelco is the principal author of Nix and undoubtedly a central figure in the ecosystem that grew around it. We confirm that Eelco showed no intention to be perceived as or act like the BDFL [Benevolent Dictator for Life] of the Nix ecosystem, or the Nix code base. To commit to that in a timely manner, he has decided to formally step down from the board.
k8s turns 10, and proved it is not Openstack
It’s quite remarkable indeed!
I had the same thought…
It doesn’t shows signs of slowing down either.
I tried OpenStack at the first few releases, after that I understood why it failed, it is a disaster lol
Well, I wouldn’t say OpenStack failed, judging by the numbers. Anyways, K8s can run on top of OpenStack, I don’t think you can really compare.
Hi all. Been a while since I posted and connected with some of the community. There is an exciting semi controversial livestream next week about DevSecOps!
Former Netflix head of security Jason Chan and Resourcely CEO Travis McPeak have a deep dive into DevSecOps.
The interview-style livestream will cover:
How DevSecOps got started Hear some real stories about adopting DevSecOps at modern organizations like Netflix What’s wrong with DevSecOps today The future for security embedded into developer workflows
https://www.linkedin.com/events/deathofdevsecops-experiencesatn7201635030605987840
2024-06-07
2024-06-10
Anyone ever have issues with setfacl commands persisting in a docker build with Github Actions with the ubuntu-latest runner? I’m setting acls, but when running the container they get lost…
IE: If you build an image with this dockerfile in Github Actions, you don’t get any ACLs, but if you build it locally, you get ACLs…. https://gist.github.com/AlexAtkinson/c57574cfad70fa50e11dd58c2b1730b5
A hint… Running that container like docker run acl-test:latest getfacl /var/cache/sit reveals that the acls exist while in github runner…. After pulling that container from ECR they no longer exist….
Pushing that docker image to dockerhub from GHA and pulling it has the same result as when pushing the image to ECR from GHA and pulling it…. No acls persisted.
I’m missing something basic.
“Docker imposes certain limitations that make working with capabilities much simpler. For example, file capabilities are stored within a file’s extended attributes, and extended attributes are stripped out when Docker images are built. This means you will not normally have to concern yourself too much with file capabilities in containers.
It is of course possible to get file capabilities into containers at runtime, however this is not recommended.
“
Either the gist is private or deleted, but I don’t understand the rationale for doing this in a container.
2024-06-11
got some time to play with NixOS and feel this distro will be the one to bridge dev and ops together
recently I took a look NixOS, it seems it will grow to be a big competitor to a few projects, like Ansible/Chef, snpad…
NixOS community needs an actor to accelerate like IBM to RedHat 25 years ago
recently I took a look NixOS, it seems it will grow to be a big competitor to a few projects, like Ansible/Chef, snpad…
Oracle should invest into NixOS community before others start
I feel like most things oracle touches get ruined by their enterprise approach of trying to make money off everything
Lol agreed, one of companies I worked for was acquired by Oracle… now it is struggling to get back the battle field with the old competitors, feeling like it is interesting if it can start with a strategic one as NixOS, then IBM and Ubuntu and SUSE will be shaking…
2024-06-12
Cloudflare Account Executive Records Herself Being Laid Off (2024): https://www.youtube.com/watch?v=u7G7OpgKROw
I know people are experiencing this kind of situation every day, I had before too. Some decision makers are stupid, e.g. the persons who decided license change in Ha$hicorp. Keep calm and Learn Open Source!
my respects to this lady
I know that CloudFlare’s CEO is hard on their sales team, but as I understand, sales is a cutthroat industry where it’s extremely easy to develop metrics for measuring employee performance and also necessary for companies to drop low performers. It’s very meritocratic and that’s a pro and a con of the field. I hope she can find work elsewhere but I don’t think the decision makers are stupid here.
To err is human, but some wouldn’t just admit, this stupid is bigger and has more impact on people during this tough time
I have been laid off recently from ServiceNow , reason project closure , not related to performance or cost cut just project closed and they don’t need me anymore.
sorry to hear that, it is tough and will last for a while under the current world political relationship, be prepared
2024-06-13
M$’s Open Service Mesh failed to compete with Istio, https://github.com/openservicemesh/osm
Open Service Mesh (OSM) is a lightweight, extensible, cloud native service mesh that allows users to uniformly manage, secure, and get out-of-the-box observability features for highly dynamic microservice environments.
Azure AKS still supports both OSM and Istio. I tested Istio/Cilium on AKS. Istio can be enabled after AKS is created but Cilium requires to recreate AKS cluster
Open Service Mesh (OSM) is a lightweight, extensible, cloud native service mesh that allows users to uniformly manage, secure, and get out-of-the-box observability features for highly dynamic microservice environments.
IIRC from various podcasts, Microsoft wanted to use Istio but felt they couldn’t commit to it given its funky governance.
There were some weird internal dynamics at Google who were trying to gain some advantage from having it outside the CNCF. I think some on the business side saw AWS getting a lot of the kubernetes benefits and wanted to keep Istio for themselves.
Istio and envoy were also a key part of the Google and GCP roadmap so they perhaps wanted more say on the initial features.
Publicly, Google was arguing disingenuously that Istio was already fully open source and had open governance (just not CNCF) so this was all FUD on Microsoft’s and IBM’s part.
Then at some point Google gave in after a few years, partly because some big customers wanted it in CNCF. At that point, OSM was no longer needed, and it never really had the featureset for adoption.
got it, felt OSM is more simple and straightforward, another M$ attempt tapping into open sources failed…
I think the community consensus is that a service mesh is mainly for big companies who need all the features that Istio has (e.g. expansion of mesh to on prem virtual machines).
Smaller companies can make do with something in between (like pod security groups on AWS, or DAPR for mtls).
I followed Cilium and Consul for a few years, even though Istio defeated OSM, the learning curve is hard, it depends on Envoy which is also not easy to configure. After eBPF is in production, Istio may face a strong competitor
good point on cilium/eBBF. Cisco is using it for its distributed HyperShield. GCP’s distributed firewall is another transparent option for L7 protection without needing to deploy a proxy - not sure if it uses cilium under the cover but more likely a mulit-tenant envoy as that’s the standard proxy Google uses corporation wide.
But yea for most people and most features Cilium/eBPF would also do the job, especially if it’s the managed dataplane by the Cloud Provider. There’s the ongoing vendor debate about whether Cilium is suitable for strong identity and multi-tenant L7 protection but they’re edge cases that only maybe some auditors and companies like Bloomberg would view as dealbreakers.
Ultimately service mesh (istio) solves around 10 problems, is expensive to rollout and requires a mature organisation. If you don’t have all 10 problems, don’t need it for regulatory purposes, and aren’t multi-cloud, there are many less expensive solutions in-between.
yes, cloud firewall is expensive, I used Istio recently to reduce the costs in a proof-of-concept project, much cheaper
2024-06-14
2024-06-15
Does anyone have experience with secrets management in IoT devices? Planning to deploy a fleet of Things that will need privileged access to a backend, and I’ll need some solution to either store secrets only in memory or invalidate them on power-loss
I’m thinking about just having a management console with SSH access to the fleet where I can manually acknowledge and authorize them after power-on to grab secrets and store in memory.
Manual, remote authorization is basically the only cost effective pattern available if you need 99% security on devices that anyone can physically access. Of course, once physical access to the device is a possibility, there is no way to prevent access to its local data, even if only stored in memory.
2024-06-17
2024-06-18
2024-06-19
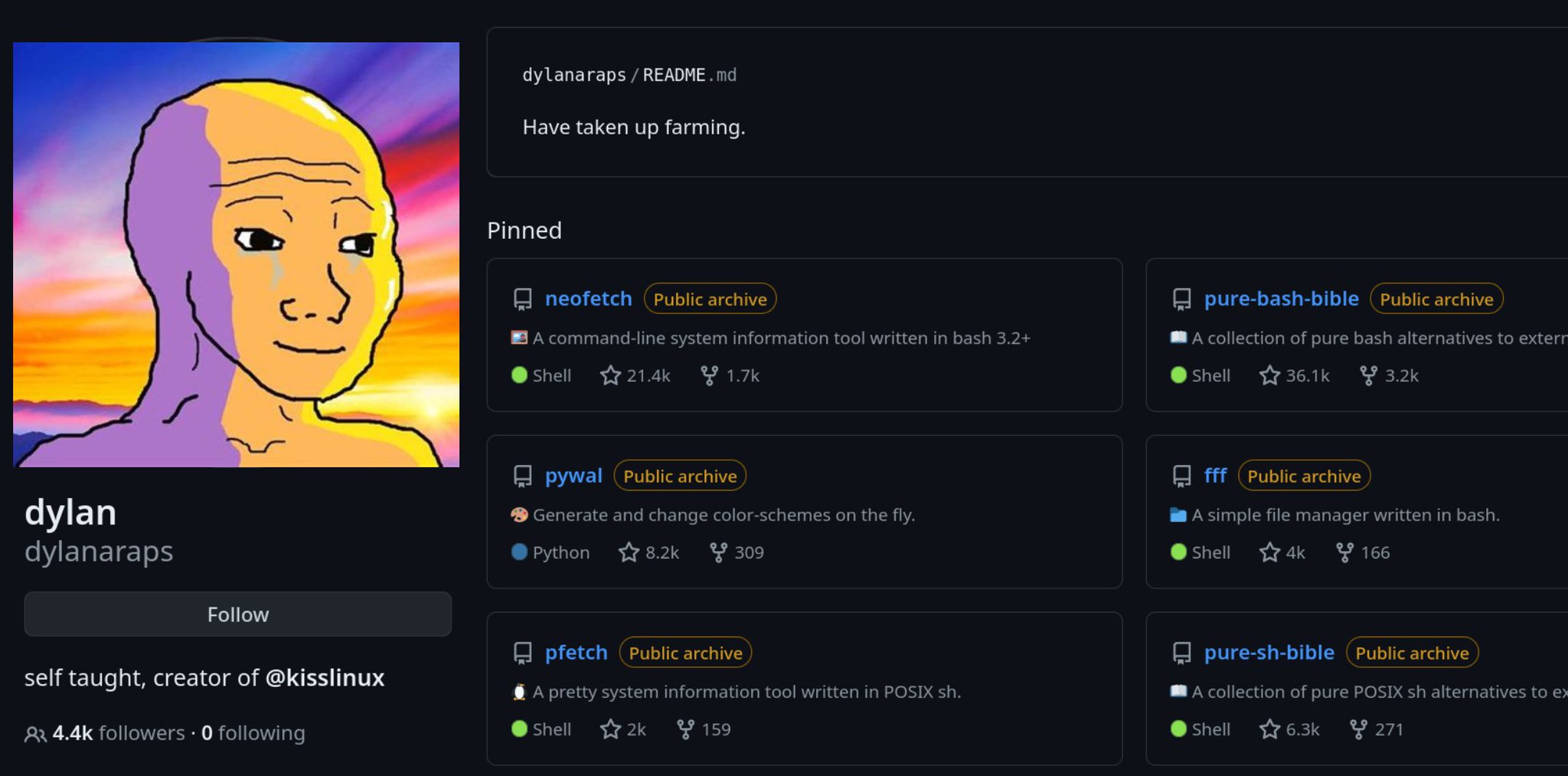
the creator of neofetch archived everything
his last commit was changing his README to “have taken up farming”
beautiful.
I’m trying to get on his level

the creator of neofetch archived everything
his last commit was changing his README to “have taken up farming”
beautiful.
2024-06-20
Anyone seeing dumb web app behavior due to the 1% affect of the 3rd party cookies phase out yet? It shows up in Devtools > Application / Cookies pane as a error. Cookies from https://... may have been blocked due to third-party cookies phaseout.
Dockerhub is having some issues https://www.dockerstatus.com/
The official status page for services offered by Docker.
Docker Hub is falling down…
The official status page for services offered by Docker.
2024-06-21
hello. what’s the status of projects stored under “https://github.com/cloudposse-archives” ? for example https://github.com/cloudposse-archives/sudosh ? It doesn’t have the “archived” status on github and there’s nothing there saying that the project is not maintained anymore. However it was moved from https://github.com/cloudposse/sudosh to https://github.com/cloudposse-archives/sudosh and the last commit dates february 2022. Is it still maintained?
@Erik Osterman (Cloud Posse)
It’s no longer maintained
We went though recently and moved projects we are no longer using or maintaining to archives. Sorry for not updating it, there were several hundred.
what alternative would you advise for sudosh?
So we implemented this as a “poor man’s” alternative to Gravitational Teleport SSH, which adds proper session recording.
This is the gold standard, and what we would recommend.
Any customer we have that requires this capability is using Teleport
Note, there’s almost nothing to sudosh. It’s a thin wrapper to sudo so it can be used as a shell.
The easiest thing is to just fork it
OK thanks for the info Erik :)
hello guys! I am doing a survey in container orchestration for academic purposes! We want your feedback by filling out this 5-minute survey about your knowledge of some orchestrators like K8s. It has no commercial purposes, and the results will be made public.
This survey is part of a study by the Faculty of Engineering of the University of Porto (FEUP) on Container Orchestration, which aims to identify and validate best practices and patterns in the field. It focuses specifically on Scheduling, Resource Management and Allocation, Configuration, and Scaling.
This study has no commercial goal, the results will be made public, ensuring accessibility for all interested. In the end of the questionnaire, you can choose to receive the results first-hand.
Estimated Time to Complete: 5 minutes
Offline alternative to Notion. Eidos is an extensible framework for managing your personal data throughout your lifetime in one place. open-source and local-first.
2024-06-24
2024-06-25
End of an era https://www.showbiz411.com/2024/06/25/paramount-shuts-down-mtv-website-wipes-history-after-20-plus-years

MTV.com is gone. Kaput. Wiped off the face of the Earth. Parent company Paramount, formerly Viacom, has tossed twenty plus years of news archives. All that’s left is a placeholder site for reality shows. The M in MTV – music — is gone, and so is all the reporting and all the journalism performed by […]
 2
2oh no, MTV is my first door to the free world

MTV.com is gone. Kaput. Wiped off the face of the Earth. Parent company Paramount, formerly Viacom, has tossed twenty plus years of news archives. All that’s left is a placeholder site for reality shows. The M in MTV – music — is gone, and so is all the reporting and all the journalism performed by […]
2024-06-26
2024-06-27
Not sure if this is just me or you have run into the similar issue before with Zoom, Yesterday Zoom reminded me to update twice. Before updates, the voice quality was no issue. After the first update, I was told that my voice was breaking, and then Zoom reminded me there will be another update. After 2nd update, the voice quality was improved but not stable.
Yesterday on Office Hours, had a UI issue with Zoom. It wouldn’t confirm that the recording would stop or start. And was persistently stuck on “Recording”. So not related, but related.
hmm this is suspicious
Zoom is definitely doing something behind the scene
yesterday seems my voice got no issue, but the other side was clear or far away
What’s the worst CSP doc you’ve seen? I just ran into this majestic failure of an endpoint strategy: https://www.intercom.com/help/en/articles/3894-using-intercom-with-content-security-policy

All Intercom domains you’ll need to allow in your CSP or firewall.
2024-06-28
Hey folks, HashiCorp is piloting a series of videos where “experts” in various domains answer questions from the field. They’ve asked me to lead the first one. A couple things I want honest feedback for:
- Is this interesting to anyone?
- Are folks comfortable asking these questions in public? (On LinkedIn/Twitter)
- Is it clear what kinds of things to ask?
- Would you want an anonymous option (and why)? Including the text for the series as well as the link in LinkedIn: Cloud automation can be confusing, often leaving people with many unanswered questions.
We’re here to change that.
Drop your toughest questions in the comments. In our new video series, ‘Let’s Talk,’ https://www.linkedin.com/in/jake-lundberg-7501271/ will dive into how people, processes, and technology impact companies’ successful start and maintenance of cloud automation efforts.

Cloud automation can be confusing, often leaving people with many unanswered questions.
We're here to change that.
Drop your toughest questions in the…
2024-06-29
You know what the 8th project in top 100 stars repo? Tip: the efforts that slaves fight back
Links from today’s office hours:
https://github.com/JFryy/qq https://github.com/glasskube/glasskube https://github.com/zsh-users/zsh-autosuggestions/tree/master https://www.nytimes.com/2024/06/24/us/politics/assange-plea.html https://roadmap.sh/terraform https://atmos.tools https://github.com/codespaces/new?hide_repo_select=true&ref=main&repo=cloudposse/atmos&skip_quickstart=true https://atmos.tools/quick-start/mindset https://atmos.tools/quick-start/simple/ https://www.redhat.com/en/topics/linux/centos-linux-eol https://slack.com/intl/en-gb/help/articles/29414264463635-Updates-to-message-and-file-history-on-free-workspaces https://terminaltrove.com/ https://lwn.net/SubscriberLink/978463/608c876c1153fd31/ https://github.com/hashicorp/terraform/releases https://github.com/ajeetdsouza/zoxide https://sansec.io/research/polyfill-supply-chain-attack?utm_source=tldrwebdev https://github.com/EvanLi/Github-Ranking/blob/master/Top100/Top-100-stars.md https://aws.amazon.com/s3/reduced-redundancy/ https://github.com/Linen-dev/linen.dev
I assume you are referring too: https://github.com/996icu/996.ICU ?
Links from today’s office hours:
https://github.com/JFryy/qq https://github.com/glasskube/glasskube https://github.com/zsh-users/zsh-autosuggestions/tree/master https://www.nytimes.com/2024/06/24/us/politics/assange-plea.html https://roadmap.sh/terraform https://atmos.tools https://github.com/codespaces/new?hide_repo_select=true&ref=main&repo=cloudposse/atmos&skip_quickstart=true https://atmos.tools/quick-start/mindset https://atmos.tools/quick-start/simple/ https://www.redhat.com/en/topics/linux/centos-linux-eol https://slack.com/intl/en-gb/help/articles/29414264463635-Updates-to-message-and-file-history-on-free-workspaces https://terminaltrove.com/ https://lwn.net/SubscriberLink/978463/608c876c1153fd31/ https://github.com/hashicorp/terraform/releases https://github.com/ajeetdsouza/zoxide https://sansec.io/research/polyfill-supply-chain-attack?utm_source=tldrwebdev https://github.com/EvanLi/Github-Ranking/blob/master/Top100/Top-100-stars.md https://aws.amazon.com/s3/reduced-redundancy/ https://github.com/Linen-dev/linen.dev
yeah, it is there for a while and this repo has been blocked from mainland if remember it correct
 1
1
And attempt to catalog Chinese companies who demand a 996 schedule—9 am to 9 pm, six days a week—is the most “starred” project on Microsoft’s code-sharing site.
Chinese tech workers rebelled against the long working day—996: 9 a.m. to 9 p.m, 6 days a week. What can workers in the US learn from them?

Since its launch on 26 March 2019, the online protest 996.ICU has attracted enormous attention, giving voice to the growing resentment against long working hours in China’s tech industry and eliciting widespread sympathy. The 996.ICU project was initiated by an anonymous user on GitHub, a Microsoft-owned code-sharing online community with more than 20 million users. […]
everyone in the world should be cautious, not only who works in tech industry. free world is not far from being slaved
the situation in that world is not improving after this repo was created, ’cause more layoffs there happened, and seldom people in free world noticed