#security (2018-12)
Archive: https://archive.sweetops.com/security/
2018-12-03
this is neat: https://privacy.com/

Checkout securely online by creating unique virtual card numbers for every purchase. Avoid data breaches, unwanted charges, and stolen credit card numbers.
2018-12-04
Today we are excited to announce the public availability of HashiCorp Vault 1.0. Vault is a tool to manage secrets and protect sensitive data for any infrastructure and application…
@antonbabenko auto unseal has arrived
About time.
Beautiful
2018-12-05
lololol
gravitational guys have reproduced the kubernetes exploit
2018-12-16
Kubernetes operator for Sysdig Falco that allows developers to manage rules for detecting intruders and backdoors - mumoshu/falco-operator
2018-12-19
Enable access to your VPC and on-premises network from anywhere, on any device.
 1
1
Two vulnerabilities discovered and patched over the summer expose Jenkins servers to mass exploitation.
oh joy!
just something in time for the holidays… a gift to the spammers & scammers for christmas
2018-12-20
yea, great timing…
I think I might prefer a git credential helper instead
haha, yea, in the end I’ll be using my OSX keychain instead
here’s where I see this as interesting: EC2 Instance “master keys”
while these should not be used for regular maintence
they can be good as a last resort
this lets you store them in a centralized place and use IAM to control who has access to them.
while also leveraging them from the command line to connect
exactly - like that
are you using vault enterprise or the community edition?
community
my understanding is they’ve added auto-unseal to enterprise
…the other way aaround
auto-unseal is now available in CE using KMS
that’s what I meant
Whoa this is really nice for the times you need a server to grab a deploy key… i had been grabbing the private deploy key from hashicorp vault or aws ssm - but then writing to a file . Didn’t think of temporary add to a ssh-agent!
Nice trick
2018-12-21
2018-12-26
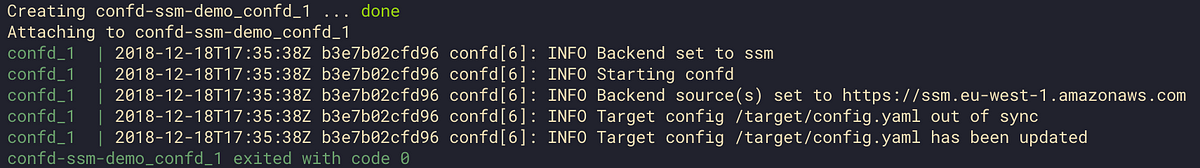
Use AWS SSM with confd to simplify application configuration management.
And then using this pattern with Kubernetes https://www.bitservices.io/blog/confd-kubernetes/
Using confd to Inject Secrets into Kubernetes Pods Whilst using Kubernetes over the past few months, one challenge I repeatedly faced was to get secrets - such as passwords, SSH keys or certificate keys - securely into applications running on Kubernetes. Whilst this is quite easy if the container image is under your full control, to achieve this with an ‘off the shelf’ image is a little more tricky.
Are k8s secrets still unencrypted in etcd?
and not at all secret?
they are encrypted at rest in etcd
that seems new since I last looked (1+ year ago)
though I guess it depends on your k8s implementation
Geodesic is the fastest way to get up and running with a rock solid, production grade cloud platform built on top of strictly Open Source tools. https://slack.cloudposse.com/ - cloudposse/geodesic
I’m not comfortable with secrets at present because they are in the clear. I attended a kubecon session on security, they talked about the encryption providers: https://kubernetes.io/docs/tasks/administer-cluster/kms-provider/
2018-12-27
Last week Troy Hunt launched his Pwned Password v2 service which has an API handled and cached by Cloudflare using a clever anonymity scheme. The following simple code can check if a password exists in Troy’s database without sending the password to Troy.

