#terraform-aws-modules (2019-07)
 Terraform Modules
Terraform Modules
Discussions related to https://github.com/terraform-aws-modules
Archive: https://archive.sweetops.com/terraform-aws-modules/
2019-07-02
In the cloudposse repos, how is the terraform.md file generated in the docs folder on the repos? Some Automated script that pulls from the variables.tf?
@jmccollum hi
this channel is not for Cloud Posse repos, it’s for https://github.com/terraform-aws-modules/
Collection of Terraform AWS modules supported by the community - Terraform AWS modules
but to answer your question, we run the following commands:
make init
make readme/deps
make readme
Ah ok, sorry about that. Thanks I’ll take a look at that.
Collection of Makefiles to facilitate building Golang projects, Dockerfiles, Helm charts, and more - cloudposse/build-harness
build-harness gets included in the repo’s Makefile, e.g. https://github.com/cloudposse/terraform-aws-key-pair/blob/master/Makefile#L6
Terraform Module to Automatically Generate SSH Key Pairs (Public/Private Keys) - cloudposse/terraform-aws-key-pair
is there a module for an ASG with a mixed instances policy?
2019-07-03
@cabrinha yes, sorta. https://github.com/bitflight-public/terraform-aws-ecs-cluster
An autoscaling EC2 cluster that can be a mixture of on demand and spot instances, or fargate - bitflight-public/terraform-aws-ecs-cluster
thanks @jamie, I think this might actually be more useful to me than the Airship module!
An autoscaling EC2 cluster that can be a mixture of on demand and spot instances, or fargate - bitflight-public/terraform-aws-ecs-cluster
Haha. It deviates a little from @maarten version to fit a project requirement I had. But I still use it since I like having spot instances built in
oh, where it says:
variable "key_name" {}
do you mean the name of the .pem file on my station?
@Blaise Pabon it means the name of the aws key you want to use. You either type in an existing one. Or generate a new key and provide that name.
 1
12019-07-08
2019-07-09
Hi guys I am running into an issue with the module terraform-aws-cloudfront-s3-cdn. I am looking to create a S3 website backed by Cloudfront. As part of the same code I am creating:
- Route53 public hosted domain
- Cloudflare NS records
- ACM cert validated by dns
All of the above works perfectly but when I add the terraform-aws-cloudfront-s3-cdn I get
Error: Reference to undeclared resource on .terraform/modules/cloudfront_s3_cdn.dns/main.tf line 5, in data "aws_route53_zone" "default": 5: depends_on = [aws_route53_zone.this]
Any ideas? Do I need to create the Route53 resources first before running this module?
@Bruce Dominguez if terraform says undeclared resources, then check if you have those resources in the code
to create an S3 website with CloudFront CDN, this might help https://sweetops.slack.com/archives/CB6GHNLG0/p1562177967452800
Hi guys, what is the best way to have an S3 bucket in website mode backed by a CDN ?
It seems like <https://github.com/cloudposse/terraform-aws-cloudfront-s3-cdn> does not support website mode
and <https://github.com/cloudposse/terraform-aws-cloudfront-cdn> does not handle S3 origins
Guys do you have idea whats wrong with subnet module which calls label?
Error: Missing resource instance key
on .terraform/modules/private_subnets.private_label/outputs.tf line 2, in output "id":
2: value = "${null_resource.default.triggers.id}"
Because null_resource.default has "count" set, its attributes must be accessed
on specific instances.
For example, to correlate with indices of a referring resource, use:
null_resource.default[count.index]
i see what the error is but is it updated to work with 12>?
@Andriy Knysh (Cloud Posse)
@Milos Backonja what module are you using? (and what terraform version?)
if you are using https://github.com/cloudposse/terraform-aws-dynamic-subnets, it’s updated to TF 0.12
Terraform module for public and private subnets provisioning in existing VPC - cloudposse/terraform-aws-dynamic-subnets
usage example https://github.com/cloudposse/terraform-aws-dynamic-subnets/tree/master/examples/complete
Terraform module for public and private subnets provisioning in existing VPC - cloudposse/terraform-aws-dynamic-subnets
Thanks @Andriy Knysh (Cloud Posse). I tried before I post message with dynamic sub-nets module and that one is working. I have issue with named subnets and multi-az subnets modules. I set terraform-null-label to version 0.14.0 (which is used in dynamic subnets module) and was able to eliminate errors regarding count , but I started to see new errors. I use terraform 0.12.x
Those are not converted to 0.12 yet
Only dynamic subnets
Thanks @Andriy Knysh (Cloud Posse) I will check out the example.
2019-07-10
Another one, I got module terraform-aws-cloudfront-s3-cdn working by creating the acm and parent zone prior to using the module. Just a quick question. Do I need to create an Alias record to now point to the created CDN?
CDN itself uses cloudfront.net domain
To access the site from your domain, you need to create an alias record
Thanks @Andriy Knysh (Cloud Posse) so I need to create an alias record X.mycompany.com to point to the cf_domain_name output (xxx.cloudfront.net).
Thanks for the help
Also is there a good fargate module?
Is it best to create an ECS Fargate resource then use the modules for terraform-aws-ecs-container-definitionand terraform-aws-ecs-alb-service-task? or is there a simpler way to provision an Fargate cluster for a simple app?
@Bruce Dominguez we have a complete working example here https://github.com/cloudposse/terraform-root-modules/tree/master/aws/ecs
Example Terraform service catalog of “root module” blueprints for provisioning reference architectures - cloudposse/terraform-root-modules
we use it to deploy atlantis on ECS Fargate
it uses https://github.com/cloudposse/terraform-aws-ecs-atlantis and https://github.com/cloudposse/terraform-aws-ecs-web-app
Terraform module for deploying Atlantis as an ECS Task - cloudposse/terraform-aws-ecs-atlantis
Terraform module that implements a web app on ECS and supports autoscaling, CI/CD, monitoring, ALB integration, and much more. - cloudposse/terraform-aws-ecs-web-app
Thanks @Andriy Knysh (Cloud Posse)
2019-07-14
Is there a way i can set a flag to enable/disable cross region replication using terraform-aws-modules/rds/aws moudle ? I do not want to enable replication in non production region but want it in production
Is anyone aware of how to do this ?
2019-07-15
any ideas about my above question ?
2019-07-16
Anyone had https://github.com/cloudposse/terraform-aws-tfstate-backend/blob/master/main.tf#L104 not set versioning correctly?
Terraform module that provision an S3 bucket to store the terraform.tfstate file and a DynamoDB table to lock the state file to prevent concurrent modifications and state corruption. - cloudposse…
Looks like it should do the right thing….but I noticed no versioning on the state bucket
from statefile ^^
Manually flipped the versioning flag on the bucket, re ran a plan, no-op
0.12 or 0.11?
0.11, using the 0.11 release of the module (0.7.0)
https://github.com/terraform-providers/terraform-provider-aws/issues/8051 sounds like what I’m seeing, in terms of TF not wanting to change it back at least
Terraform Version Terraform v0.11.11 provider.aws v1.59.0 Affected Resource(s) aws_s3_bucket.s3 Expected Behavior When someone makes a manual change to S3 resource by enabling versioning, I expect …
Not sure why it was never set though..
While I remember, can we get a new release of https://github.com/cloudposse/terraform-aws-iam-account-settings/releases cut?
Terraform module to provision general IAM account settings - cloudposse/terraform-aws-iam-account-settings
2019-07-19
what’s the recommended pattern for dealing with security groups for ec2 instances? should i create them in their own plan?
Why not create them along with the instance(s)? There is a good module on the registry for security groups
hey, thanks, i found it and used it. very good module indeed, aims to implement all features… nice!
question and it may be because i’m new to tf, but using https://github.com/cloudposse/terraform-aws-rds/releases 0.9.0 - copying and pasting the example as-is i’d expect tf plan to more or less work as-is knowing i obviously need to assign the sg’s and subnets. but i’m getting more than that (attached in thread).
Terraform module to provision AWS RDS instances. Contribute to cloudposse/terraform-aws-rds development by creating an account on GitHub.
Terraform module to provision AWS RDS instances. Contribute to cloudposse/terraform-aws-rds development by creating an account on GitHub.
$ tf version
Terraform v0.12.5
any pointers accepted while i continue to debug here.
seems bound to tf version: https://github.com/terraform-aws-modules/terraform-aws-rds/issues/111
Hello, The module is not compatible with terraform 0.12-beta-1 Is anyone working on this? If not would you be interested in making a branch ? I think it only needs some minor syntax tweaks. e.g. Er…
We are converting the module to TF 0.12 now
The current module doesn’t work with 0.11
0.12 sorry
thanks for the response! will hold tight - thank-you
2019-07-20
2019-07-22
2019-07-29
does anyone know what the aws elasticbeanstalk config option CONFIG_SOURCE is for? I can’t find any aws documentation on it. https://github.com/cloudposse/terraform-aws-elastic-beanstalk-environment/blob/01d405201c192ee1948ea97bff6742140b1cfbba/main.tf#L707
Terraform module to provision an AWS Elastic Beanstalk Environment - cloudposse/terraform-aws-elastic-beanstalk-environment
Hey Folks, Trying to find some Terraform Modules related to AWS - app stream service ( for creating fleets and stacks) any help appreciated
2019-07-30
So I’m thinking of installing a private gitlab …. and before I cobble together these modules to reproduce their reference config (see diag below), I wanted to check here to make sure there wasn’t a better way:
hmmm, it looks like this tutorial may do the trick, thanks https://medium.com/@aloisbarreras_18569/architecture-overview-of-gitlab-on-aws-d260c16a2ad7
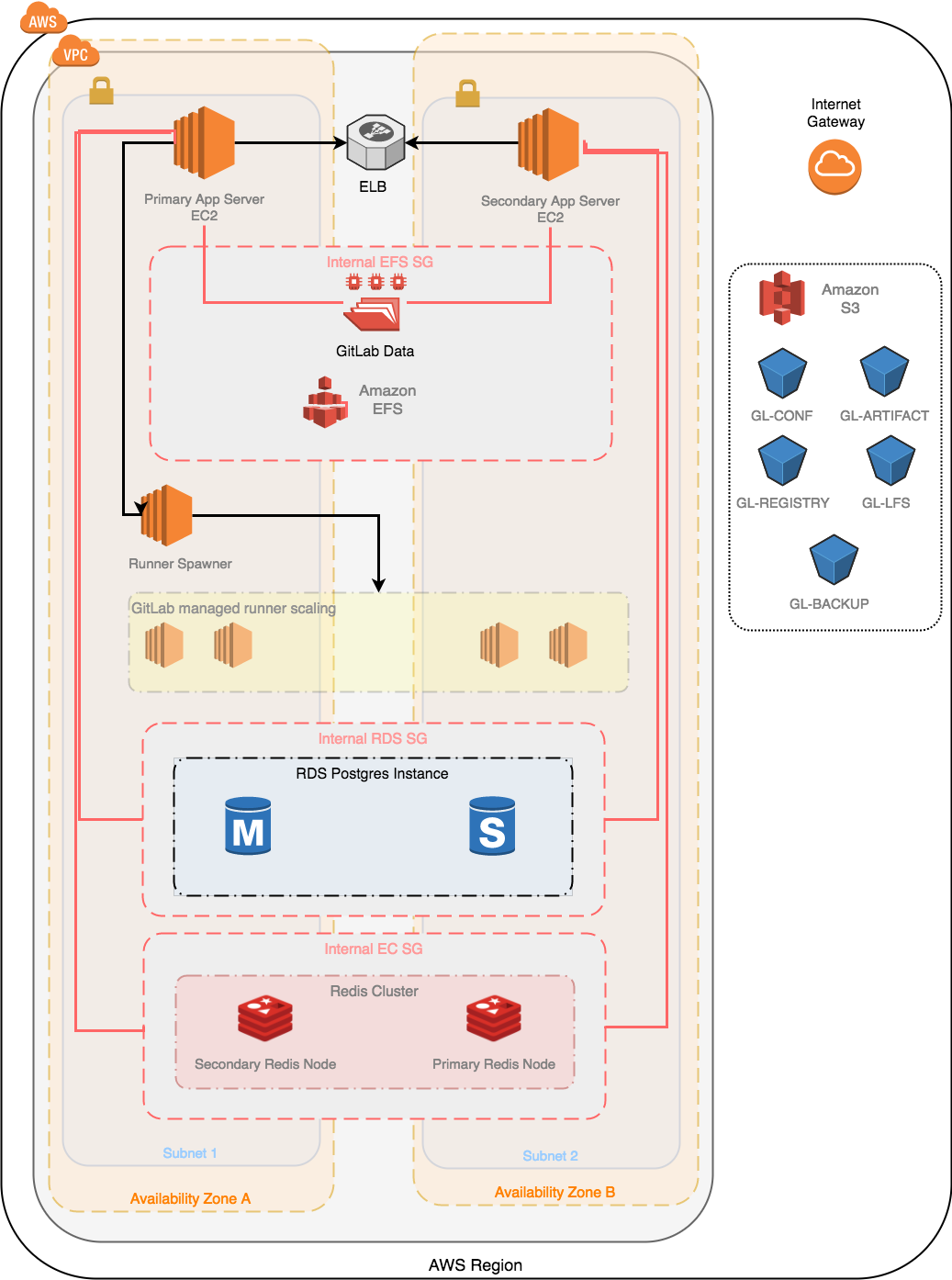
This is Part 1 of the Comprehensive Guide to Running GitLab on AWS. In the intro post to this series, we discussed why Alchemy uses GitLab…
Would need export for old gitlab installation and import for such a new environment.

This is Part 1 of the Comprehensive Guide to Running GitLab on AWS. In the intro post to this series, we discussed why Alchemy uses GitLab…
In this case, I have no existing gitllab, so the whole installation would be new.